Check out Luise Freese’s sketch note from Paula Januszkiewicz’s keynote: Attacks of the Industry: A View to the Future of Cybersecurity
About Paula:
Paula Januszkiewicz is a CEO and Founder of CQURE Inc. and CQURE Academy. She is an IT Security Auditor and Penetration Tester, Cloud and Datacenter Management MVP and trainer (MCT), and Microsoft Security Trusted Advisor. She is also a top speaker at many well-known conferences including TechEd North America, TechEd Europe, TechEd Middle East, RSA, TechDays, and CyberCrime, often rated as number-one speaker. She is engaged as a keynote speaker for security-related events and writes articles on Windows Security. She drives her own company, CQURE, working on security-related issues and projects. Paula has conducted hundreds of IT security audits and penetration tests, some for governmental organizations. Her distinct specialization is on Microsoft security solutions – she holds multiple Microsoft certifications, and is familiar with and possesses certifications in other related technologies. Paula is passionate about sharing her knowledge with others. In private, she enjoys researching new technologies, which she converts to authored training’s. What is more, she has access to the Windows source code!
Keynote Description:
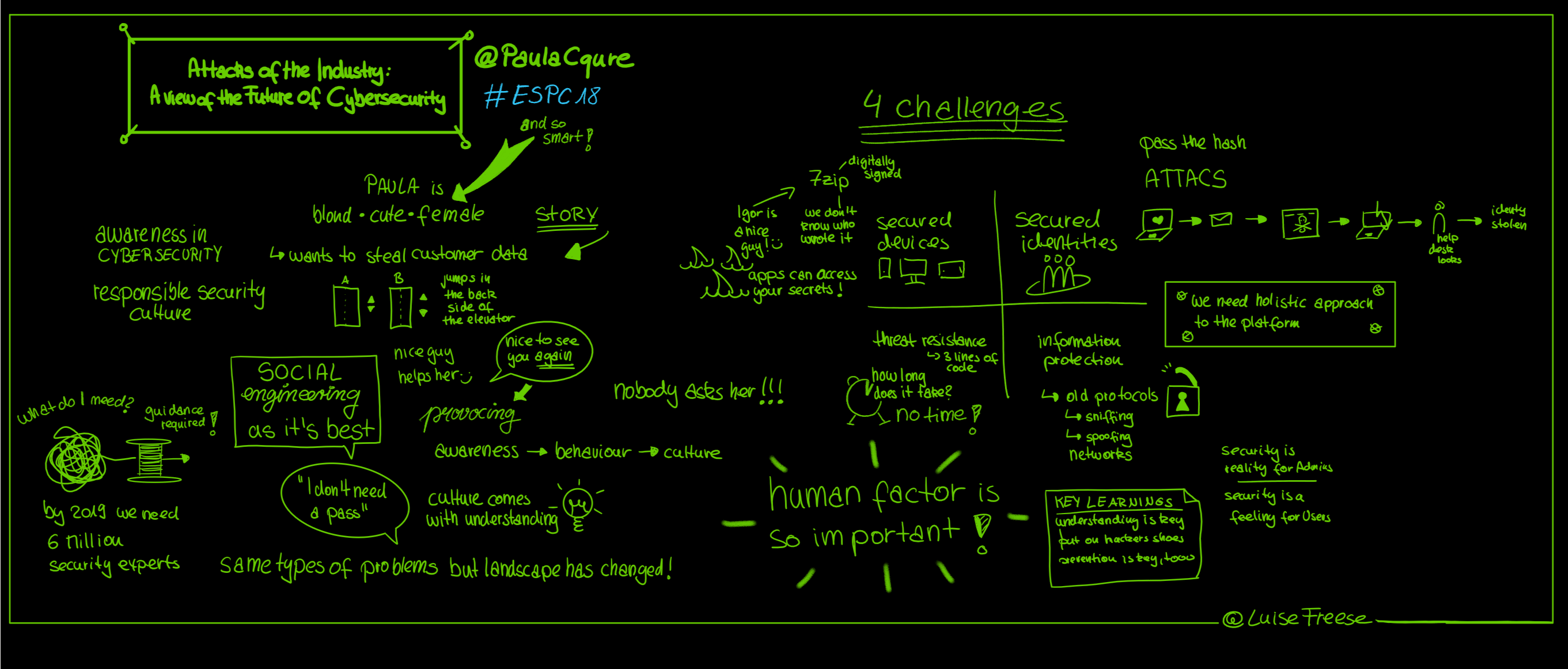
(Right click and open in a new tab for a larger image)










