Lateral Movement
In this blog post, I will be talking about Azure advanced threat protection lateral movement capability, and how this can extremely help you get a unique perspective on how attackers can move across your network and elevate their access once they compromise one your sensitive accounts. Furthermore, Azure ATP and Windows Defender ATP integration gives you the full picture once you determine a lateral movement inside your network. You can also read about Azure advanced threat protection deployment and Azure ATP vs ATA blog posts.
THE EMERGE OF ADVANCED PERSISTENT THREATS APT
Stopping cyberattacks is the number one priority for everyone, especially that security is now a discussion that is happening in boardroom and not the server room anymore. Enterprises are learning in the hard way that all their defenses techniques will never be 100% perfect, while today’s security teams are evaluated by their ability to keep the network safe against cyberattacks. The ability to quickly and reliably detect attackers and lateral movement inside corporate networks is one of the most important, and emerging skills in information security today.
Advanced persistent threats (a.k.a APT) can sidestep cyber security defenses and cause huge damage to organizations. A skilled and determined cybercriminal can use multiple vectors and entry points to navigate around defenses, breach your network in minutes and evade detection for months. Statistics shown in RSA conference 2016 demonstrated how APT attacks can gain access to organizations within minutes, and maintain access to victim networks for almost a year. [Source, RSA Conference “The Pivot”, by Jonathan Trull”]
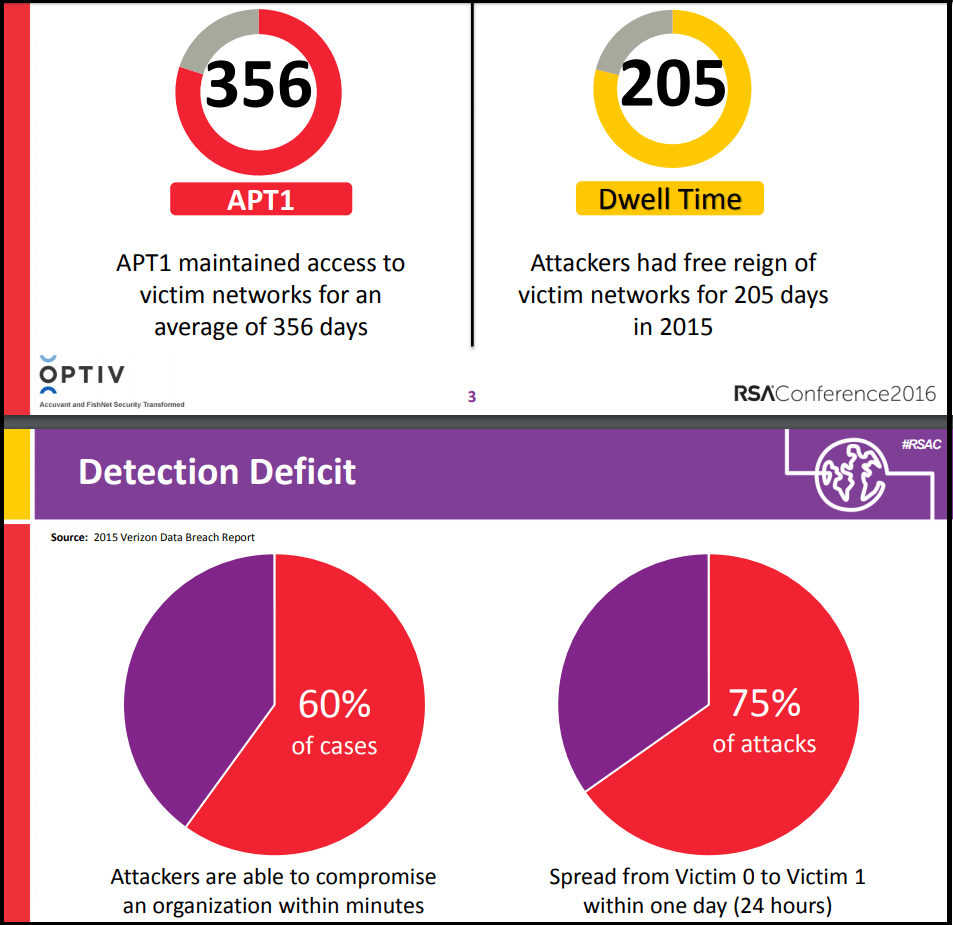
APT Attacks
What I see in most organizations, that they become busy collected tons of security events, manually chasing down policy violations and detecting anomalies. However, detecting lateral movement should move up to become the top priority as it gives an immediate indicator of an internal threat that is trying actively move around and compromise high profile resources.
Attackers usually do not start by attacking a high value asset, as those usually are well protected, or they simply do not know what is considered a high value asset yet. They start by getting themselves inside the network, by attacking a vulnerable machine or compromising an identity for a normal user. From there, attackers start to learn about the network and jump from machine to machine, until they reach a privileged account. Moving from machine to machine and from a resource to another in order to reach a high privileged account or resource is called Lateral Movement.
“Network Lateral Movement, or what is more commonly referred to simply as, “Lateral Movement“, refers to the techniques cyber attackers, or “threat actors”, use to progressively move through a network as they search for the key data and assets that are ultimately the target of their attack campaigns”. Source Wikipedia.
Lateral movement usually requires the attacker to move from device to device, escalate privileges until they reach their target [one of the sensitive accounts you configure in Azure ATP]. Not only will attackers move from device to another, thy will try to get additional points of control inside the compromised control. This will help them maintain persistence if they are discovered on the initial infected machine [patient zero]. This lateral movement is one of the clearest differentiators between a targeted attack and a commodity threat.
During lateral movement, an attacker who already compromised one machine, will try to move to a target vulnerable node. This one-sided approach forces attackers to reveal themselves, and is a golden opportunity for the security team to detect them, if they are looking in right places and for the right things.
While most security teams focus on malware detection, attackers become more smart and their attack techniques are always evolving. Nevertheless, attackers need real-time remote and control center over network devices to do lateral movement. This can be in the form of one or more specialized remote administration tools. Therefore, the behavior of an external attacker controlling an internal network is something that can quickly be recognized. This is also highly related to internal reconnaissance or suspicious activity that should immediately raise a red flag.
Identity theft and elevated privileged is a key part of lateral movement, as it makes it easy for the attacker to reach high value asset. Needless to say, stealing, reusing or impersonating a valid user give the attacker a quieter and subtler way to move around. Pass-the-hash and pass-the-tickets are famous techniques that can be used to jump between devices.
As a result, security solutions should focus on intelligence that can recognize all phases of persistent attacks, especially lateral movement. Such intelligent should rely on behavioral analytics like signing on from abnormal devices, or anomalies in users activity. Furthermore, detection of credential theft should be in place to detect inside attackers. All this require not only automated tools, but intelligence based on AI and machine learning that can digest million of logs, and come up with a threat protection model for lateral movement and APT attacks.
THE ANATOMY OF AN ATTACK AND AZURE ATP
As you can see in the picture below [taken from Microsoft blog post here], Azure advanced threat protection (a.k.a Azure ATP) has detection technique for almost all phases of the attack. It can do this by detecting anomalies in the behavior of a user or device combined by its ability to determine predefined suspicious activities. Together, both techniques help reducing the false positive signals, and enhance the quality of alerts.
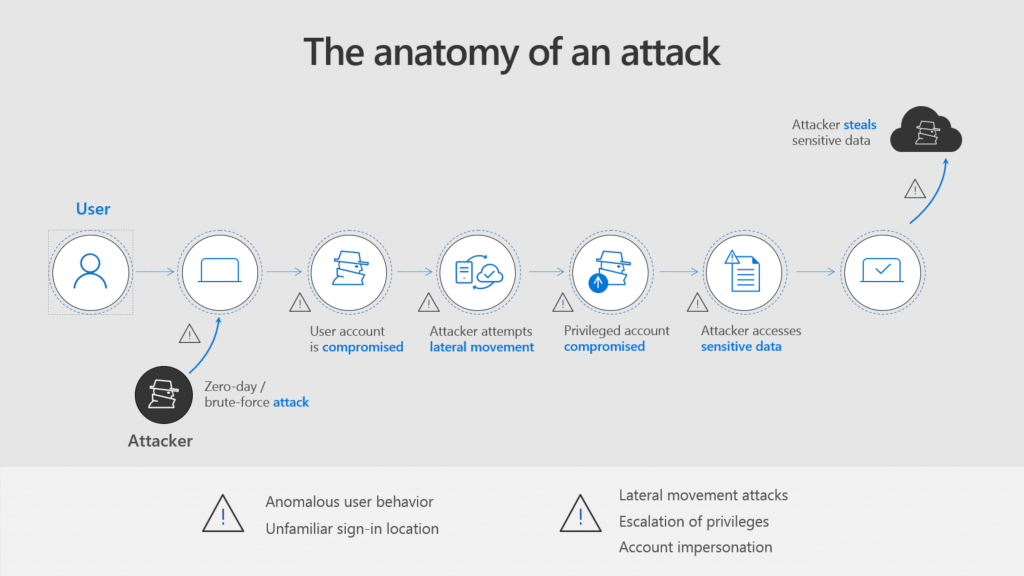
The anatomy of an attack
AZURE ADVANCED THREAT PROTECTION LATERAL MOVEMENT: DETECTION TECHNIQUES
Think about it for a second. When attackers compromise a vulnerable device inside your network, they need to MOVE around for several reasons. Moving between devices and resources usually happen within a security context (identity). For example, an attacker gain admin right on a device, he can get the hash of the logged-on user (there are a lot of stored and available credentials on Windows devices), and he tries to move the ticket or hash to access other devices.
So, attacker movement is tight to identity movement, and this is the key concept that Azure ATP is trying to leverage. Azure ATP tries to monitor how identity is being used within an enterprise, and establish a baseline (who access what usually, what times, from which devices, etc.), and from there it can detect anomalies and suspicious activities that most attackers try to do.
Windows Defender ATP from the other side, works on the endpoint level, by detecting anomalies based on the normal behavior of processes inside a machine, and why a specific process is trying to elevate its rights or talk to a remote command and control center. Azure ATP and Windows Defender ATP integration provides a comprehensive and unique insights about suspicious activities from the endpoint and identity perspective.
Azure Advanced Threat Protection can detect many signs of persistent attacks and suspicious activities inside your network as shown in the below images. For example, if it sees that there is a replication request that is coming from a computer that is not a domain controller, it will immediately trigger an alert, as attackers might initiate a replication request, allowing them to retrieve the data stored in Active Directory, including password hashes.
Azure ATP also monitors sensitive groups and can detect if there are any changes on their membership, which is a typical scenarios when attackers want to elevate their rights or leave a backdoor.
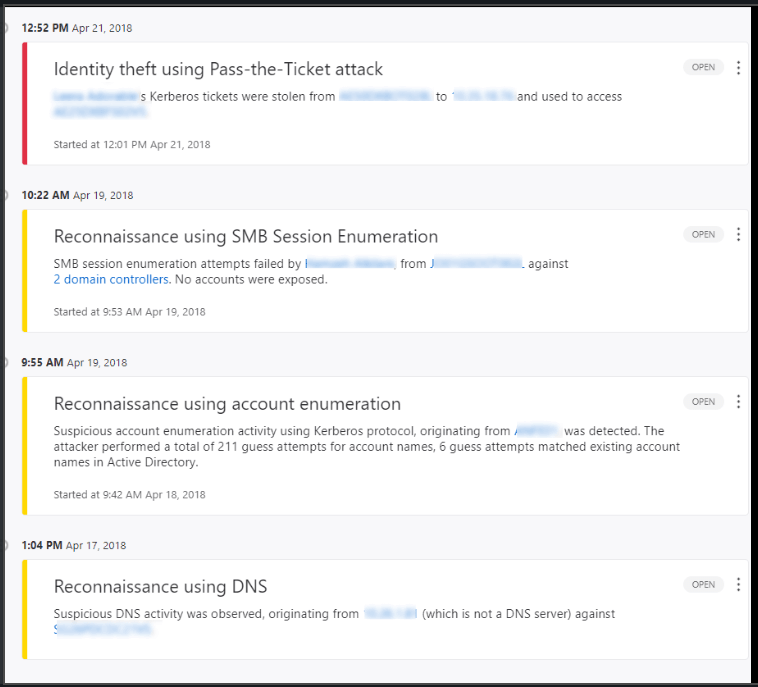
Monitoring sensitive groups
Azure ATP also uses behavioral analysis to detect anomalies inside your network. It can do that by reading all logs, observing all traffic coming to your domain controllers, and slowly building a model of how your organization behave in terms of who usually access what, from which endpoints and times. Such model is continuously adapting to changes in the network to reduce false positives. So, if Azure ATP sees that John is authenticating from unfamiliar locations, this might raise a flag, but if this is combined with another known suspicious activity like trying to do SMB session enumeration against a DC, then we have two clues here to raise the severity of the alert raised. (unfamiliar sign in location + suspicious activity)

Advanced threat detection
AZURE ADVANCED THREAT PROTECTION LATERAL MOVEMENT TIPS
Azure advanced threat protection lateral movement prevention techniques is all about slowing down attackers who are already inside the network and trying to move from host to another, until they compromise a high value asset.
Paula Januszkiewicz, one of the famous faces nowadays when it comes to cybersecurity, published a short but informative 15 minutes video on how it is possible to move between machines inside a corporate network, once an attacker gain admin privileges on one machine. This is a simple yet enough evidence for you to realize that once the attacker has admin privilege on a machine, then it is a matter of time usually for him to escalate his privileges inside your network and move around freely.
Attackers can dump the memory and read credentials in clear text most of the time, or easily get hashes of every logged-on user to that machine. Hashes are considered password equivalent as they can be passed around. Pass the hash is not a weakness in Windows, but a design decision to facilitate single sing on.
What you can quickly realize from this, is how easy it can be for the bad guys to steal hashes. Let me give you two examples.
JUMP SERVERS
Many organizations use some sort of Jump server, or TS server inside their data center, so that admins can log on there and do their administrative tasks. This also can be a terminal server that serve end users with business applications installed on it. In either case, this is considered the big prize for attackers.
Furthermore, we have a normal user who logs-on to the TS server. His credentials might be already compromised before logging on, or during his logon session. Usually normal users do not have admin rights on the terminal servers, but most of them do, as they might need to install some tools themselves. In either case, the attacker is able get admin rights on the TS in a way or another.
Now Mark [network admin] logs on to the TS server. Since the attacker has admin rights on the TS, he can easily comprise the session of Mark and get his password hash or tickets. Since Mark is local administrator on other servers in the data center, then the attacker is now moving freely within the network. Imagine if Tom [the domain admin) logs on that TS, then it is game over.
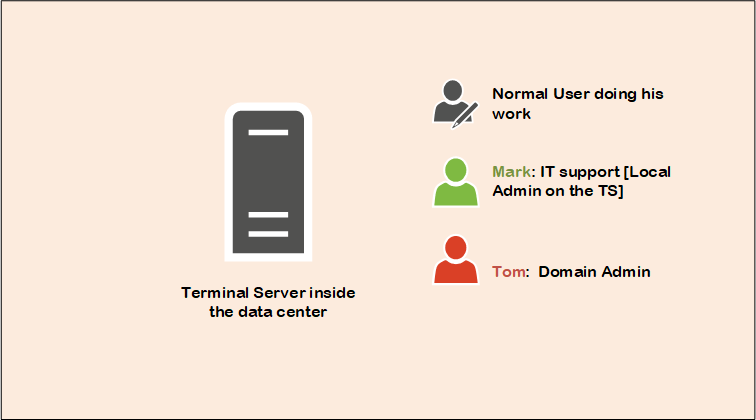
Terminal Server
LOG ON TO MACHINES WITH ADMIN RIGHTS
This is one of the famous cases I see all around. You might find that normal users are administrators on their machines, which makes attackers super happy as they do not need to elevate rights on that box. Only a small phishing attack and they are in. You might also see the same password for the local administrator account across all machines, which gives the attacker a golden chance to move around if they can remotely connect between devices.
Christina is a normal user who gets a phishing email. Within minutes, the attacker could get to her machine and elevate his rights to admin rights. He starts doing bad things to the box, so that Christina can ask Mark (local IT support) to come and help. Mark notices that Office is slow, so he tries to re-install it by supplying his admin account. The attacker now has compromised Mark account and can move to high value resources.
The key point to remember when it comes to lateral movement is to carefully consider where sensitive accounts log on to, as anyone who is member of the local administrators group of that device, might be able to steal some sort of their credentials.
So how Azure ATP can help here from prevention perspective? As you know already, Azure ATP has a concept of Sensitive Accounts. Azure ATP will classify many built-in groups as sensitive like domain admins, and all members of those groups by default. Furthermore, you can manually tag a group or users as sensitive accounts from within Azure ATP management portal.
AZURE ADVANCED THREAT PROTECTION LATERAL MOVEMENT GRAPH
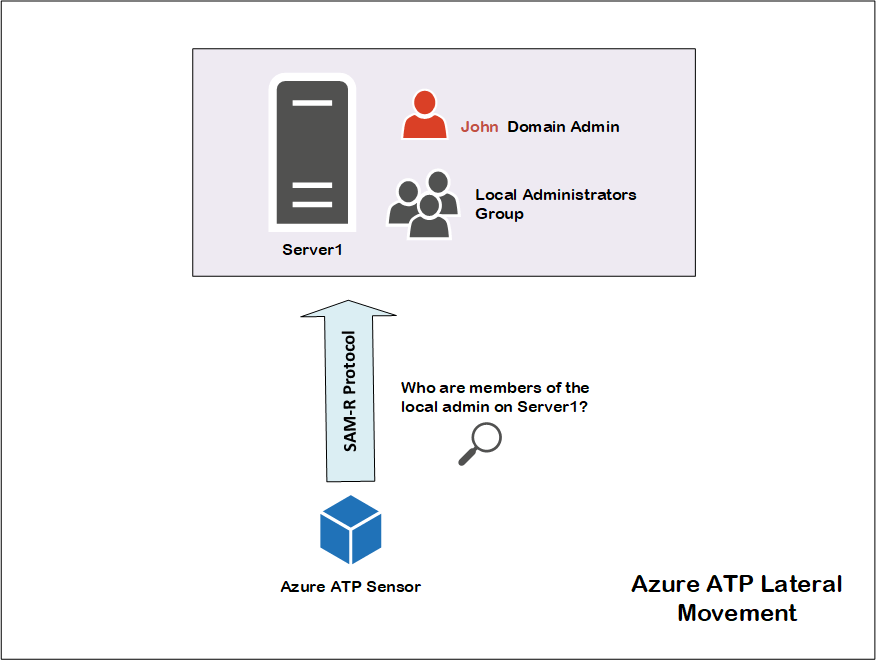
Azure ATP will do the following whenever any user who is marked as sensitive account logs on:
- Say that John Smith is marked as Sensitive Account in Azure ATP as he is member of the domain admins group
- John logs on to Server1.
- Azure ATP sensors using its service account, will try to connect to Server1 to query members of the local administrators group on that server using SAM-R protocol, given that you allowed it to do so.
- Azure ATP immediately knows that any member of the local administrators group on Server1 can compromise the identity of John. Azure ATP will start to observe where those members log on to, and who are the admins on servers they log on to.
- From there, Azure ATP will be able to draw lateral movement graph for John, showing how an attacker can compromise his identity, given the actual servers he logged on to recently [last 2 days].
Azure ATP Lateral Movement
Let us look at the picture below, showing Azure advanced threat protection lateral movement graph. Samira Abbasi is tagged as a sensitive account. This tagging could happen by Azure ATP if Samira is member of a sensitive group like domain admins, or she can be tagged manually by the Azure ATP administrator because she is the CEO of the company.
Samira usually logs in one of the Development server called REDMOND-WA-DEV to follow up with a new application that is under development. What happens next is very interesting.
Immediately after Samira logged in that server, and because she is tagged as sensitive account, Azure ATP will connect to that server using SAM-R protocol and query the members of the local admin group on that server.
Azure ATP recognized Oscar as part of the local admin group on REDMOND-WA-DEV, so it starts paying attention to Oscar (who is not tagged as sensitive account) because Oscar can compromise the identity of Samira. This fact that Oscar can compromise the identity of Samira comes from two observations that Azure ATP did:
- Samira did actually log in REDMOND-WA-DEV.
- Oscar is member of the local admin group on that server.
Azure ATP will start to investigate Oscar account, by consider him a temporary sensitive account. Azure ATP detects that Oscar just logged in to REDMOND-WA-DEV2, and immediately will query the local admin group on that server too.
Azure ATP learned that both Contoso All and Contoso IT are member of the local admin group on REDMOND-WA-DEV2. This means that any one who is member of those two groups can theoretically compromise Oscar’s account, and from there he can compromise Samira’s account.
The question for this organization to ask is, on the machine that Samira is logged on to, why is Contoso All group a member of the local administrators group. It can be configuration error!
Those discussions that is happening because you saw such lateral movement graph, will help organizations get more insight and perhaps take some measures to reduce the chance of lateral movement.

Microsoft Advanced Threat Analytics
KEY OBSERVATIONS
- Azure advanced threat protection lateral movement graphs are predication on how such movement can happen.
- Lateral movement graph works side by side with your definition of sensitive accounts.
- This graph has an interesting arrow type, which is highlighted in green in the picture [Logged on to by], which means that someone did actually log on somewhere. Therefore, The only actual logon activities in the previous lateral movement graph are:
- Samira logging in to REDMOND-WA-DEV
- Oscar logging in to REDMOND-WA-DEV2
- The graph shows that any member of [Contoso All or Contoso IT] COULD log on to REDMOND-WA-DEV2, which Oscaractually logged on to recently. From there, anyone member of the previous groups can steal Oscar credentials because they are admin on DEV2. Oscar from the other hand COULD log on to REDMOND-WA-DEV as he is an admin there. What makes this interesting is that Samira logged on to the REDMOND-WA-DEV recently, which could allow the attacker to compromise her identity.
- Anyone who is member of Contoso ALL or Contoso IT can compromise the identity of Samira, if they do bad things at the right time and place. Moreover, any attacker who compromises the identity of anyone who is member of Contoso All or Contoso IT can do the same.
HOW TO STOP LATERAL MOVEMENT IN YOUR ENVIRONMENT
While Azure advanced threat protection lateral movement graphs can help you see possibilities for an attack to reach sensitive accounts, you can slow down such movement by implementing couple of counter-measures.
USE STANDARD USER ACCOUNTS
Use Standard User Accounts: Enforce users to have standard user accounts on their machines. Administrators also should log in with their standard accounts [so administrators should have two accounts, their standard account, ad their admin account].
LEAST PRIVILEGE PRINCIPLE
If someone does not need access to systems or applications, remove that access. Give only those privileges which are essentials to perform intended function. Microsoft published a great guide to help you implement his principle [Implementing Least-Privilege Administrative Models].
IMPLEMENT MFA FOR SENSITIVE ACCOUNTS
While mos people out there recommend the use of MFA for sensitive accounts, or [Require smart card] option enabled for such account, I can argue that this will not prevent a persistent attacker from stealing the hash of a logged on user.
Even worse, if someone has the [Require smart card for interactive logon], then his NTLM hash the get generated for the password once this potion is enable will never be changed or expire, so an attacker who already stole that hash, can enjoy a long standing access.
RANDOMIZE LOCAL ADMIN PASSWORD
You should not have the same local admin password on your machines and especially your servers, as this will make lateral movement so easy to accomplished. Microsoft has a tool called LAPS or Local Administrator Password Solution that can help in this regard. Do not use group policies to set the local admin password on machines using scripts or GPO preferences as attackers can easily get access to those passwords as published here.
HARDEN YOUR WORKSTATIONS
- Enable local firewall on all workstations at least for incoming traffic – enforce this via GPO and do not allow local rules to apply, only rules from GPO. [Allow local firewall rules = false]
- Create a security baselines and apply it to your workstations. Microsoft has great documentation about this here.
- Prevent workstations from being accessed using CIFS or SMB, and prevent workstations to share files between them or share printers. All sharing and printing capabilities should happen on a file and a print server. So, you cannot do \\PC1\C$ by any means on your workstations. Doing this will significantly help mitigate pass-the-hash and malware spread inside your network.Here is an example of a GPO that will do that by disabling the Computer Browser and Server services , and setting a registry key under LanManServer registry hive.

Workstations
PROTECT DOMAIN ADMINS
I highly recommend to create a separate account for each domain admin in your network, and never share the same domain admin account. Also, you should have as an admin three accounts:
- Your normal account.
- Your admin account on servers [Exchange admin, Server admin,…]
- Domain admin account [ Remove it from being the admin on all machine, and create a GPO to deny domain admins from logon locally on all servers and workstations except domain controllers]
The last point is super important. Your domain admin account should rarely be used, and you should not be able to log on to any machine except domain controllers using your domain admin account.
DENY LOCAL ACCOUNT FROM NETWORK LOGON
- Start by renaming your local admin account on workstations and server to something like Viva, while this will not change the SID for the admin account, it is at leas a starting point.
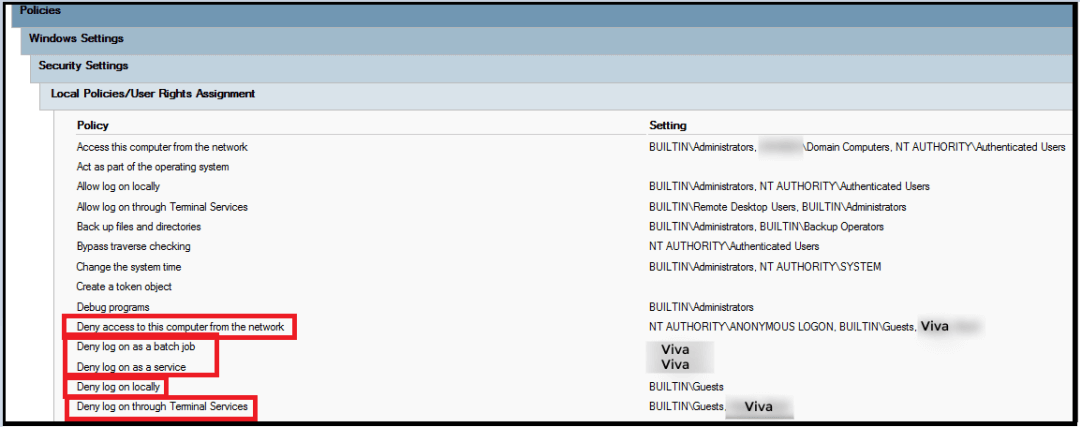
- Create a GPO that restrict what the local admin can do on machines and servers as per the following:
You can see here a GPO to rename the administrator account to VIVA and the guest account to CAT [again this will not change the SID, so easy for attacker to guess them], we also disable the guest account.

Computer Configuration
This GPO will do a lot of things:
- Deny access to this computer form the network: We have the BUILTIN\Guests and VIVA [remember this is the local admin account we just renamed]
- Deny log on as a batch job>VIVA
- Deny log on as a service> VIVA
- Deny log on locally > BUILTIN\Guests
- Deny log on through Terminal Services> BUILTIN\Guests and VIVA
Policies
IMPLEMENT THREAT AND ADVANCED BEHAVIOR MONITORING
When it comes to prevention techniques, Microsoft did a great work in the new versions of Windows 10 when it comes to Virtualization-based Security (VBS) solutions like Credential Guard, Device Guard and Application Guard. Windows Defender is a serious thing to consider and look at carefully as Microsoft is putting great investments there. Just have a look at Exploit Guard, App Control and other amazing features in Windows like Windows Information Protection (WIP), Windows Hello for Business, BitLocker, APP Locker and more.
While all that can help you protect your data and endpoint, there will always be a way for attackers to get into your network, and compromise credentials. Now organizations need to step up their security plans from traditional security defenses to a true behavioral analytics, machine learning and AI, which is considered the future of security detection techniques.
Microsoft has three ATP products that work together to help you protect, detect and respond to advanced persistent attacks API:
- Office 365 ATP [Integrates with Windows Defender ATP] : Protect attacks coming from emails and uploaded to SharePoint Online.
- Windows Defender ATP [Integrates with the other two ATPs]: Protect endpoints and devices, now comes with automated responses.
- Azure ATP [integrates with Windows Defender ATP]: protect identities and detect suspicious behaviors/anomalies.
One thing to remember, Azure advanced threat protection lateral movement graph is a way to predict how attackers might move to compromise sensitive accounts, and is not a detection technique. Azure advanced threat protection lateral movement depends on your definition on sensitive accounts, so make sure you configure them well. Finally, Azure advanced threat protection lateral movement depends on the ability for Azure ATP sensors to connect remotely to machines that sensitive accounts log on to, and pulling the membership of the local administration group.
I believe Azure advanced threat protection lateral movement graphs are valid for two days, so that it shows possible lateral movements within 2 days from a logon activity of a sensitive account.
Azure ATP
RESOURCES
Azure advanced threat protection lateral movement is an important feature that you should pay attention to. Here are some resources that I find interesting.
Azure AP vs ATA blog post and Azure advanced threat protection deployment guide.
Also, I found it interesting that Microsoft published an attack simulation guide for ATA which should work fine for Azure ATP. Wade Williamson also published an a good article in April 2016 talking about “Lateral movement: when cyber attacks go sideways“.
Microsoft blog post “Ransomware lateral movement, and how Microsoft Advanced Threat Analytics can help” is a good resource to look at.
Finally, there is a very detailed and valuable whitepaper published by the computer emergency response team by the name “Detecting Lateral Movements
in Windows Infrastructure“. This whitepaper explain in great detail all what you need to know about how to detect lateral movement.
Reference:
Hasayen, A. (2018). Azure Advanced Threat Protection Lateral Movement. Available at: https://blog.ahasayen.com/azure-advanced-threat-protection-lateral-movement/ [Accessed: 8 May 2018]