Instead of pure lift-and-shift migrations to the cloud, we often encounter lift-shift-tinker migrations. Azure AD Seamless Single Sign-On (Seamless SSO) automatically signs in users when they are on their PCs or devices that are connected to their organisation network.
In such a migration, you modify some of the application components to take advantage of cloud services. Often, that’s the database but it could also be your web servers (e.g. replaced by Azure Web App). When you replace SQL Server on-premises with SQL Server or Managed Instance on Azure, we often get the following questions:
- How does Azure SQL Database or Managed Instance integrate with Active Directory?
- How do you authenticate to these databases with an Azure Active Directory account?
- Is MFA (multi-factor authentication) supported?
- If the user is logged on with an Active Directory account on a domain-joined computer, is single sign-on possible?
In this post, we will look at two distinct configuration options that can be used together if required:
- Azure AD authentication to SQL Database
- Single sign-on to Azure SQL Database from a domain-joined computer via Azure AD Seamless SSO
In what follows, I will provide an overview of the steps. Use the links to the Microsoft documentation for the details. There are many!!! 😉
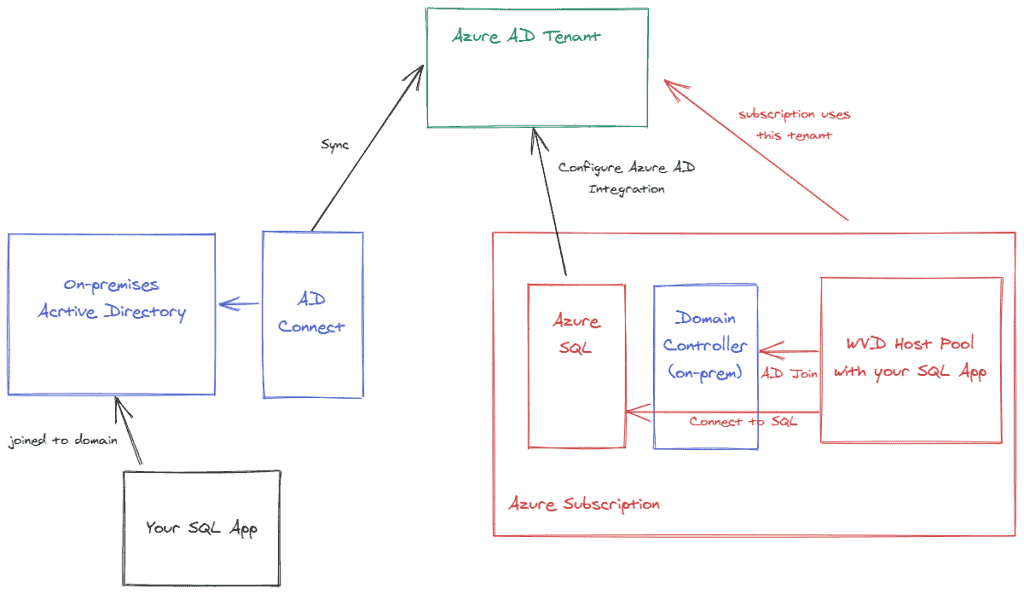
Visually, it looks a bit like below. In the image, there’s an actual domain controller in Azure (extra Active Directory site) for local authentication to Active Directory. Later in this post, there is an example Python app that was run on a WVD host joined to this AD.
Azure AD Authentication
Both Azure SQL Database and Managed Instances can be integrated with Azure Active Directory. They cannot be integrated with on-premises Active Directory (ADDS) or Azure Active Directory Domain Services.
For Azure SQL Database, the configuration is at the SQL Server level:
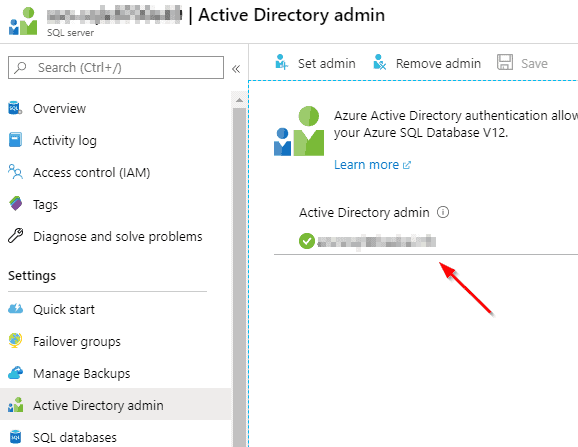
You should read the full documentation because there are many details to understand. The account you set as admin can be a cloud-only account. It does not need a specific role. When the account is set, you can logon with that account from Management Studio:
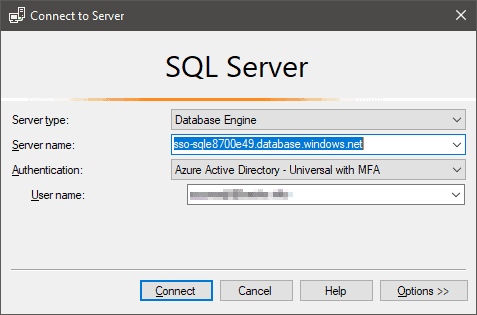
There are several authentication schemes supported by Management Studio but the Universal with MFA option typically works best. If your account has MFA enabled, you will be challenged for a second factor as usual.
Once connected with the Azure AD “admin”, you can create contained database users with the following syntax:
CREATE USER [user@domain.com] FROM EXTERNAL PROVIDER;
Note that instead of a single user, you can work with groups here. Just use the group name instead of the user principal name. In the database, the user or group appears in Management Studio like so:
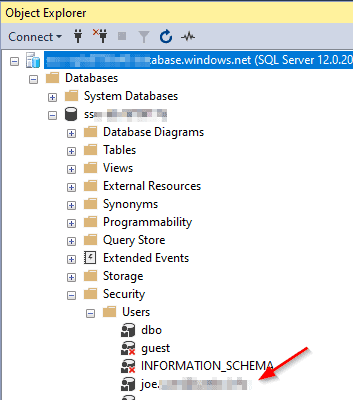
From an administration perspective, the integration steps are straightforward but you create your users differently. When you migrate databases to the cloud, you will have to replace the references to on-premises ADDS users with references to Azure AD users!
Seamless SSO
Now that Azure AD is integrated with Azure SQL Database, we can configure single sign-on for users that are logged on with Active Directory credentials on a domain-joined computer. Note that I am not discussing Azure AD joined or hybrid Azure AD joined devices. The case I am discussing applies to Windows Virtual Desktop (WVD) as well. WVD devices are domain-joined and need line-of-sight to Active Directory domain controllers.
Note: seamless SSO is of course optional but it is a great way to make it easier for users to connect to your application after the migration to Azure
To enable single sign-on to Azure SQL Database, we will use the Seamless SSO feature of Active Directory. That feature works with both password-synchronization and pass-through authentication. All of this is configured via Azure AD Connect. Azure AD Connect takes care of the synchronization of on-premises identities in Active Directory to an Azure Active Directory tenant. If you are not familiar with Azure AD Connect, please check the documentation as that discussion is beyond the scope of this post.
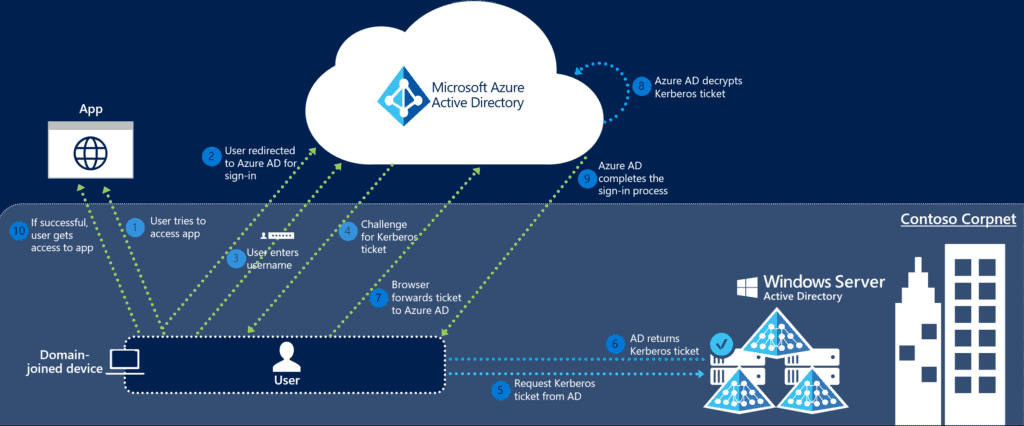
When Seamless SSO is configured, you will see a new computer account in Active Directory, called AZUREADSSOACC$. You will need to turn on advanced settings in Active Directory Users and Computers to see it. That account is important as it is used to provide a Kerberos ticket to Azure AD. For full details, check the documentation. Understanding the flow depicted below is important:
Before trying SSO to Azure SQL Database, log on to a domain-joined device with an identity that is synced to the cloud. Make sure, Internet Explorer is configured as follows:
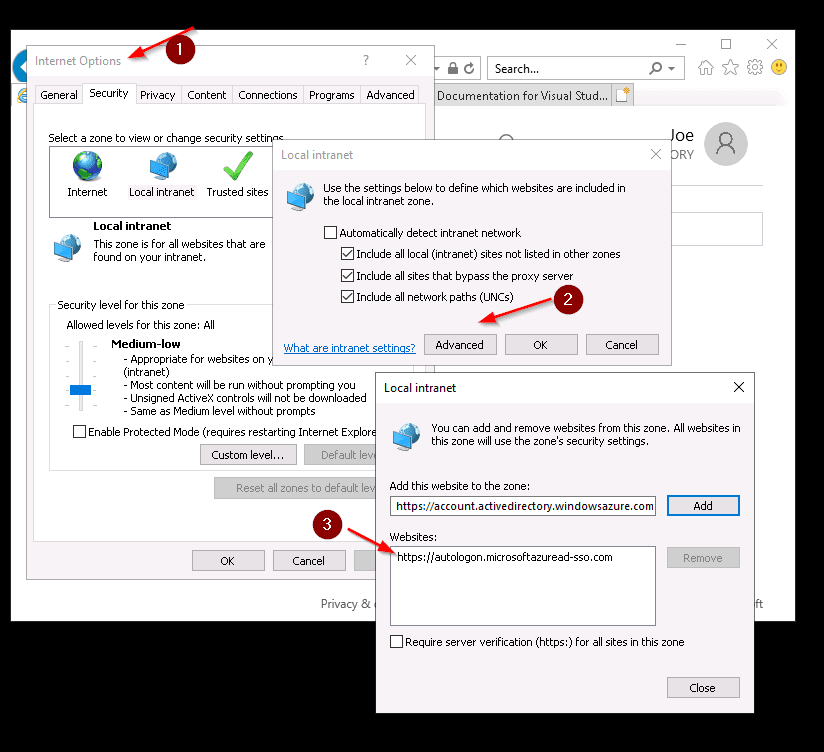
Check the docs for more information about the Internet Explorer setting and considerations for other browsers.
Note: you do not need to configure the Local Intranet zone if you want SSO to Azure SQL Database via ODBC (discussed below)
With the Local Intranet zone configured, you should be able to go to https://myapps.microsoft.com and only provide your Azure AD principal (e.g. first.last@yourdomain.com). You should not be asked to provide your password. If you use https://myapps.microsoft.com/yourdomain.com, you will not even be asked your username.
With that out of the way, let’s see if we can connect to Azure SQL Database using an ODBC connection. Make sure you have installed the latest ODBC Driver for SQL Server on the machine (in my case, ODBC Driver 17). Create an ODBC connection with the Azure SQL Server name. In the next step, you see the following authentication options:
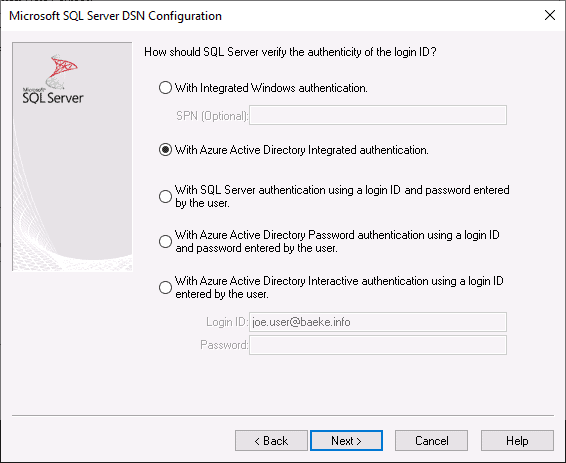
Although all the options for Azure Active Directory should work, we are interested in integrated authentication, based on the credentials of the logged on user. In the next steps, I only set the database name and accepted all the other options as default. Now you can test the data source:
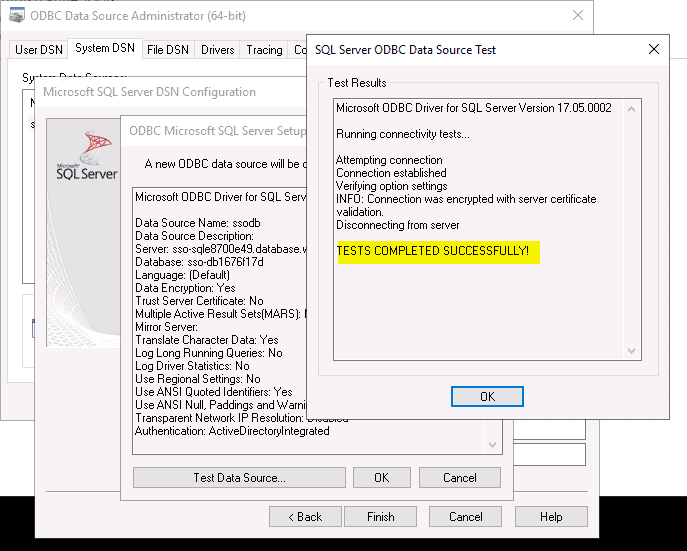
Great, but what about your applications? Depending on the application, there still might be quite some work to do and some code to change. Instead of opening that can of worms 🥫, let’s see how this integrated connection works from a sample Pyhton application.
Integrated Authentication test with Python
The following Python program uses pyodbc to connect with integrated authentication:
import pyodbc
server = 'tcp:AZURESQLSERVER.database.windows.net'
database = 'AZURESQLDATABASE'
cnxn = pyodbc.connect('DRIVER={ODBC Driver 17 for SQL Server};SERVER='+server+';DATABASE='+database+';authentication=ActiveDirectoryIntegrated')
cursor = cnxn.cursor()
cursor.execute("SELECT * from TEST;")
row = cursor.fetchone()
while row:
print(row[0])
row = cursor.fetchone()
My SQL Database contains a simple table called test. The logged on user has read and write access. As you can see, there is no user and password specified. In the connection string, “authentication=ActiveDirectoryIntegrated” is doing the trick. The result is just my name (hey, it’s a test):

Conclusion
In this post, I have highlighted how single sign-on works for domain-joined devices when you use Azure AD Connect password synchronization in combination with the Seamless SSO feature. This scenario is supported by SQL Server ODBC driver version 17 as shown with the Python code. Although I used SQL Database as an example, this scenario also applies to a managed instance.
Reference:
Gaeke, G. (2020). Azure SQL, Azure Active Directory and Seamless SSO: An Overview. Available at: https://blog.baeke.info/2020/05/02/azure-sql-azure-active-directory-and-seamless-sso-an-overview/ [Accessed: 17th May 2020].
Check out more great Azure content here