As part of Microsoft’s Zero Trust strategy, Conditional Access has been the central control mechanism in Azure AD to define which kind of access controls must be fulfilled to access cloud apps that are integrated with Azure AD. However, until now it was not possible to define more granular controls. With Conditional Access Authentication Context this changes. You can now require step-up authentication if a user performs a certain action or accesses sensitive information.
What actions / cloud apps are in scope?
At the moment, you have the following options to use Authentication Context.
- Microsoft Cloud App Security (MCAS): require step-up authentication as part of an MCAS session control policy
- Microsoft Information Protection: require Authentication Context to access labeled content (part of the groups & sites labeling feature, not file-based)
- SharePoint Online: Authentication Context can be assigned to SPO sites via PowerShell
- Build you own applications with Authentication Context support
Keep in mind that this is a public preview, so functionality might increase over time. Support for Azure AD PIM is already announced
Defining an Authentication Context
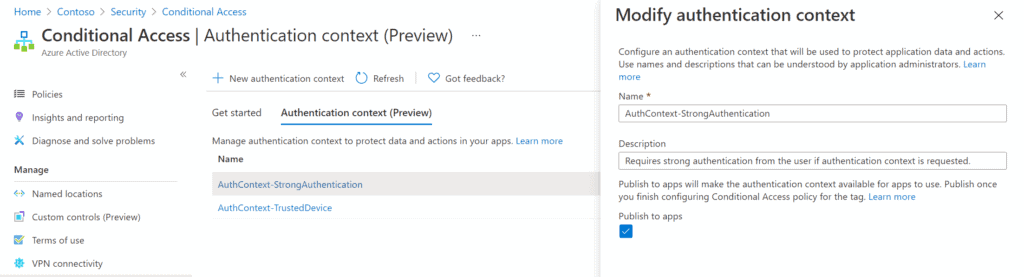
First, we need to configure the Authentication Context. For itself, Authentication Context is just an empty container with a name and a description:
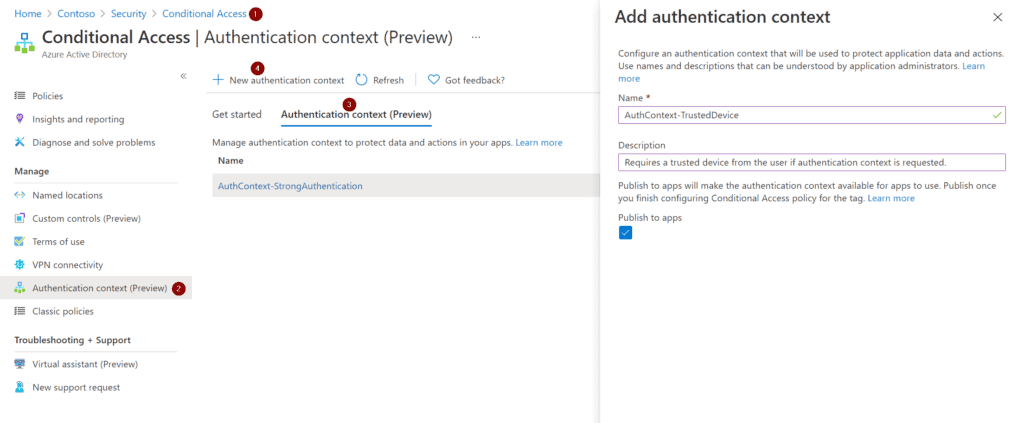
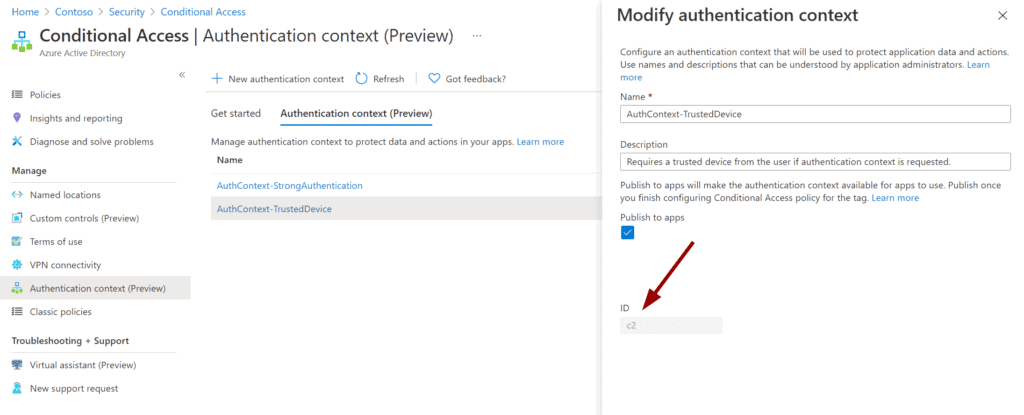
After saving we can see that every Authentication Context has an ID that can be referenced e.g. for custom app development:
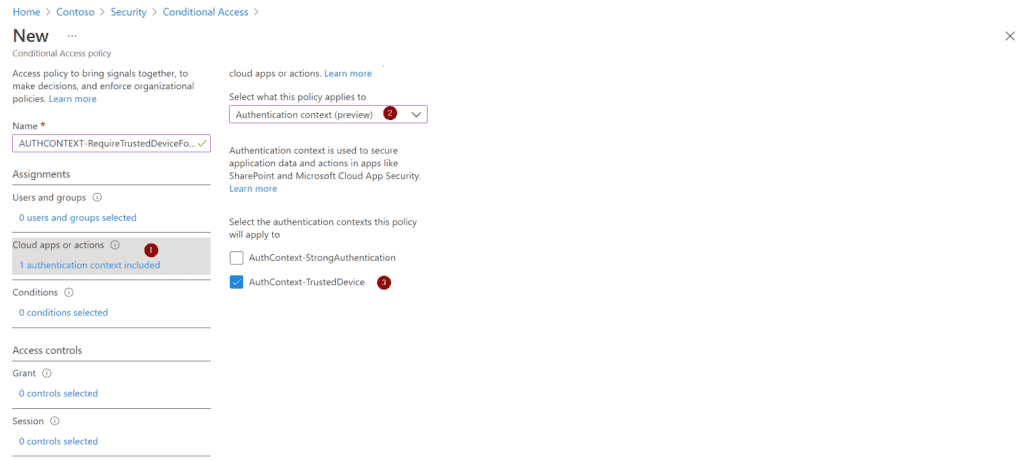
Now we need to build a Conditional Access policy that links the Authentication Context with the required access controls. If you want to go even more granular you can of course configure other conditions like device platform or client apps.
Next, we define the access controls for this Authentication Context. In this case one of the trusted device options:
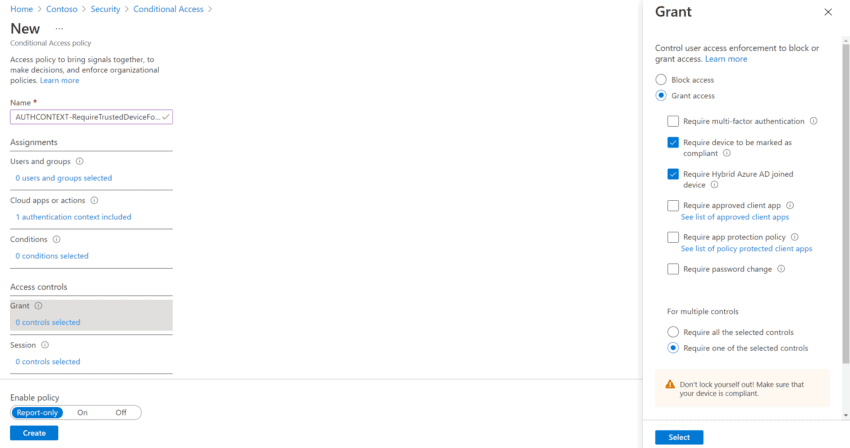
The Authentication Context is now linked to the “trusted device” access control. Whenever the context is triggered, a user will need to work on a trusted device to continue with the action you want to protect.
As an MFA prompt is a bit more interactive for a demonstration, we will continue with the other Authentication Context I already prepared that requires MFA:
Authentication Context and Microsoft Cloud App Security
Let’s have a look at how we can integrate Authentication Context with Microsoft Cloud App Security. In this case we need to use session control to benefit from step-up authentication. So we need a Conditional Access policy that redirects the user to session control. I did that for my demo user Adele:
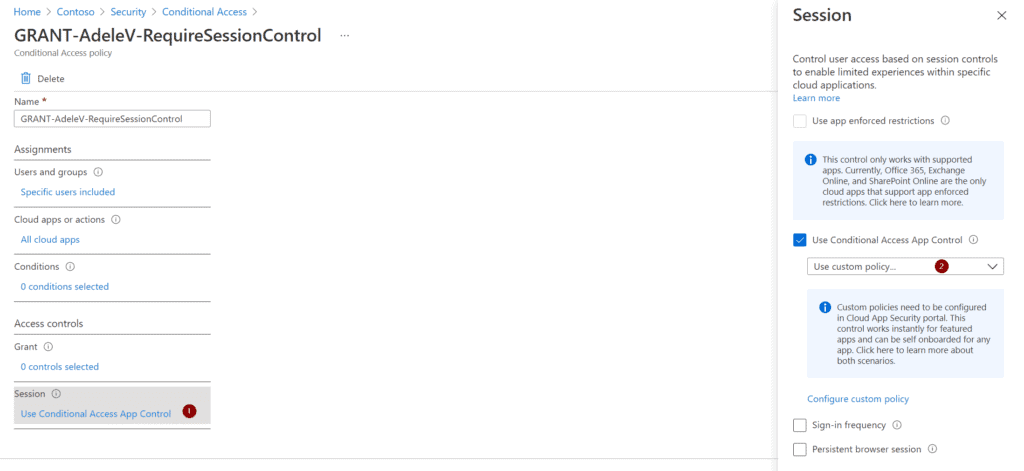
Now we head over to Microsoft Cloud App Security where we will create a session policy:
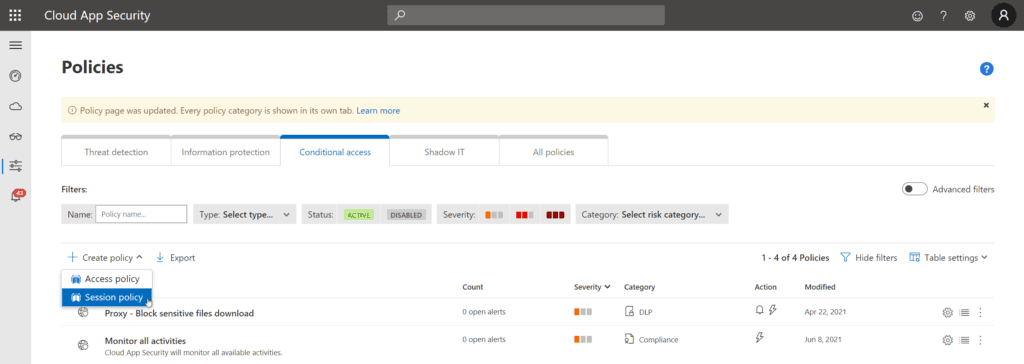
For this demo, I created a policy that requires step-up authentication for downloading “.docx” files:
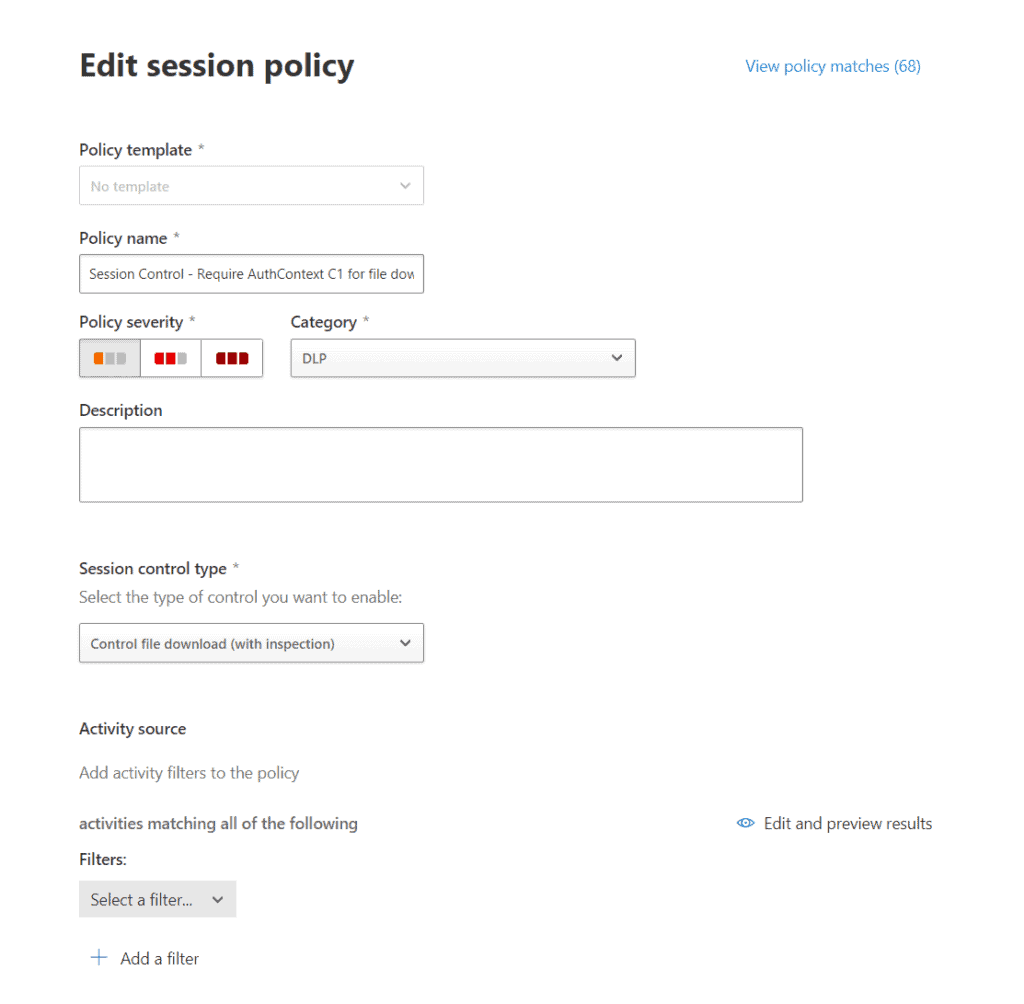
Of course you can adjust the filters to your needs. Adele will now be required to successfully complete MFA as part of the Authentication Context when downloading “.docx” files. Let’s have a look!
The user experience (with MCAS)
Adele will now sign-in to the Office portal:
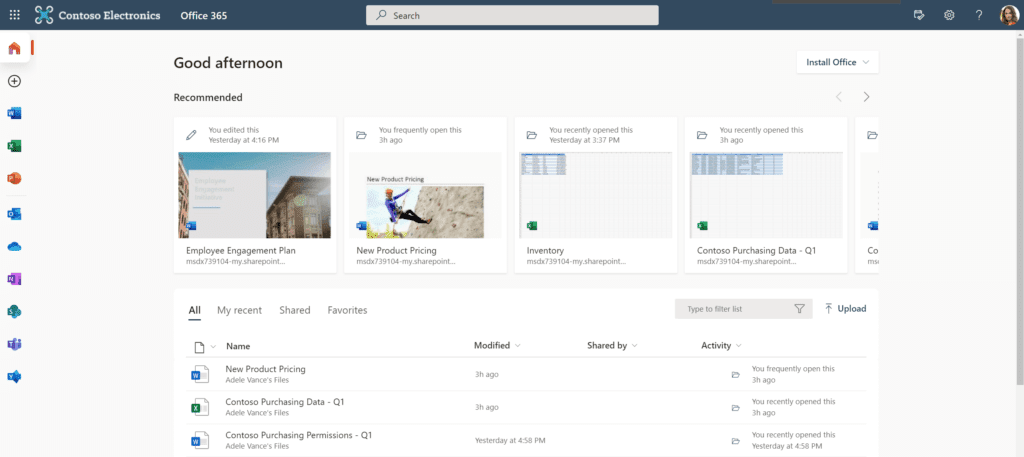
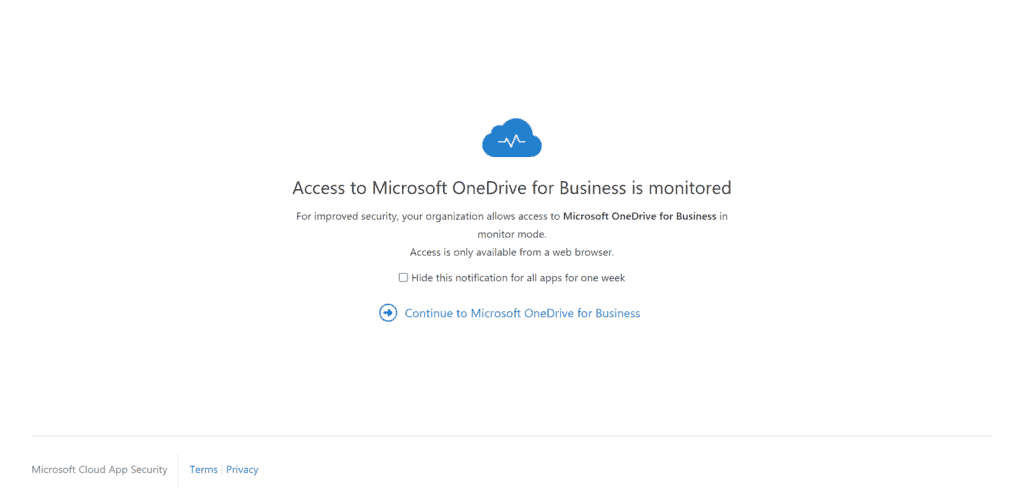
She switches to her personal OneDrive and will be notified that the session is monitored by Microsoft Cloud App Security:

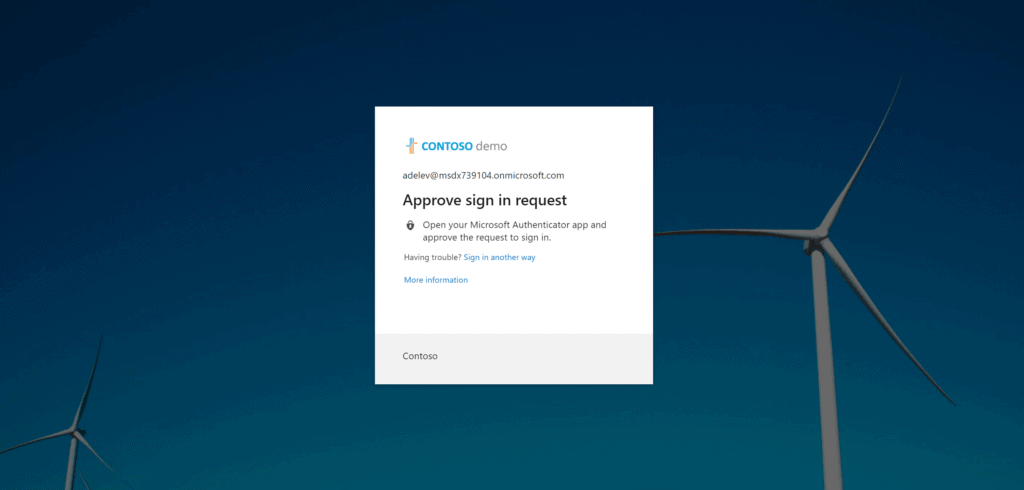
The standard MFA prompt will appear:
The check is complete:
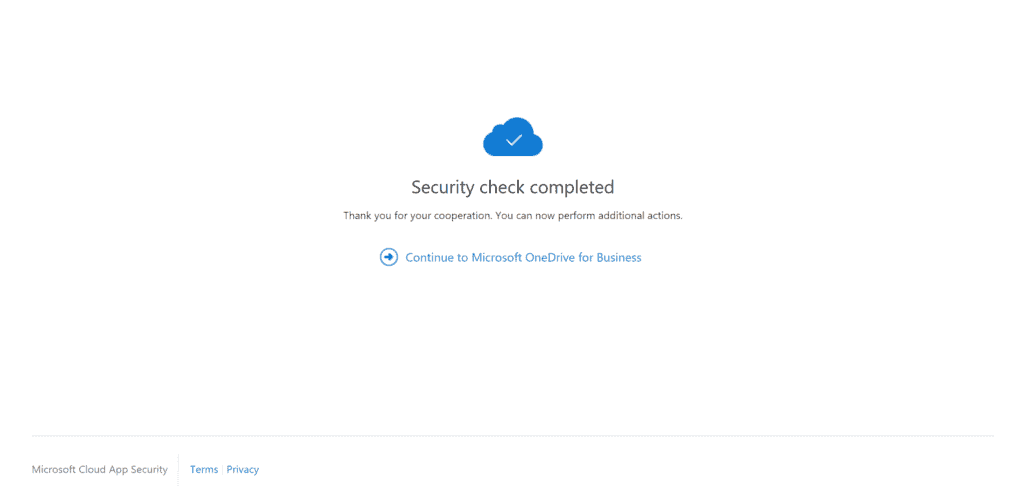
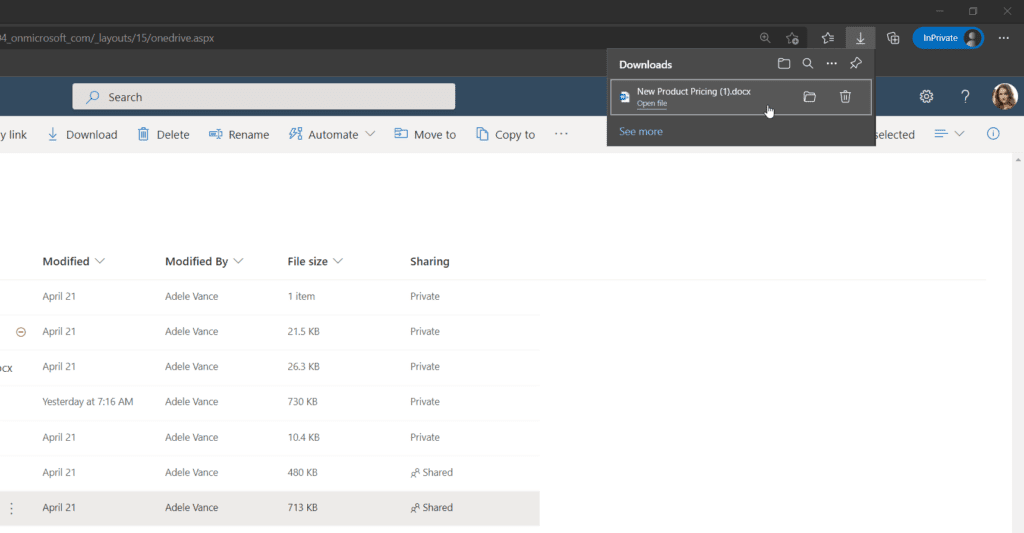
The relevant part here is “You can now perform additional actions”. Adele is now able to start the download again but it won’t start automatically after MFA was completed. The download now works:
Note
The action (download of “.docx” files) we have secured will be allowed for Adele as long as the MFA claim remains in the access token. Depending on other configuration that lifetime might be different.
Summing things up
Conditional Access is a crucial part of every tenant security setup. With Conditional Access Authentication Context we can now define much more granular control for accessing certain types of information. What this also means is that we now have a variety of technical controls to restrict access. In practice, the most challenging part will be to select the one most suitable for the scenario.
Thanks for reading!
Chris
This blog is part of Azure Week. Check it out for more great content!
About the Author:
“Hello there! My name is Christian Müller. I am working as an Senior Security Consultant at German Microsoft partner Skaylink. You can find me here:
Twitter: https://twitter.com/chrisonsecurity
LinkedIn: https://www.linkedin.com/in/christian-h-mueller/
Reference:
Müller, C. (2021). Conditional Access Authentication Context – Protect sensitive data. Available at: https://chrisonsecurity.net/2021/06/09/conditional-access-authentication-context-protect-sensitive-data/ [Accessed: 7th July 2021].