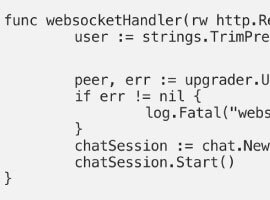
WebSocket, Redis and Go – Learn How to Build a Chat Application
Blog PostsThe WebSocket protocol offers a bi-directional (both server and client can exchange messages) and full-duplex (server or client can send messages at the same time) communication channel that makes it suitable for real-time scenarios such as chat applications etc. The connected chat users (clients) can send messages to the application (WebSocket server) and can exchange messages with… READ MORE