A major challenge in businesses is a misconception, that data is 100% secure concerning any part of its data processing within that business. This data processing concerns the content management lifecycle; from creation, to storage, to distribution, to workflow and eventually archive of that data. The misconception? “Security Breach? Its not going to happen to us” mentality. It is vital that there is an understanding of Information security and Information Assurance in content management security. As an information security professional (or Architect covering security), you should be prepared for any aspect of secure breach can happen that can affect the confidentiality, availability, and integrity of the data. Any service delivery disruption caused by a security breach is harmful to the profitability, and has far reach consequences which could include liability, status and much more.
Information security is recognised as a major area of importance in the management of organisational information systems. Losses resulting from computer abuse and errors are substantial; information systems managers continue to cite security and control as a key management issue. Service Delivery (automation, data governance, data processing, support), aligns to Information Assurance (IA) and concerns all content management systems. Security in content management systems like SharePoint (whether ‘on-premise’ or in Office365) living in the sea of an Enterprise Roadmap is particularly important to understand; concerning the protection of data, and how to understand data value, its lifecycles; and how to apply assurance. The following guide is designed to explain Information Assurance, and further guides will be made available to explain application of Information Assurance.
What are principles and concepts of Information Assurance (IA)?
In adopting IA practices; to plant the principles and concepts, there are no right or wrong choices. The selection depends on the relevant organisational requirements and regulations. This section will state concepts and principles.
Principles
To understand the principles, there needs to be an understanding about data processing (from a strategic perspective). Data processing in an organisation exists within a larger organisational framework. Data processing must be subject to organisational controls, concerning the life cycle of any system, and the data held, from the point data is created, to the point data is dissolved. There must be control exercised by the data processing management, the control function and library processing.
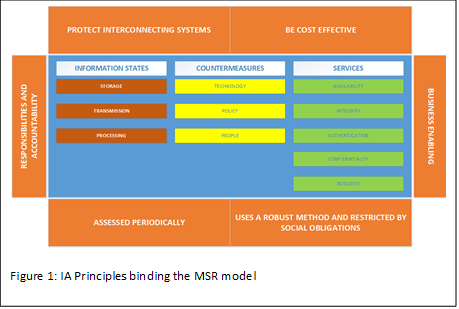
Content Management Systems – Principles
There are principles assigned to IA best practice which are related directly to ensuring organisational controls. Figure 1 shows the IA principles surrounding the Maconachy-Schou-Ragsdale model (MSR) of IA, a common model used to allow organisations to speak a common language and objectives for IA . The outside boxes of the diagram point out the key principles. The three core elements; information states, countermeasures and services, helps the data processing organisation bind those elements to any data processing system. For each of those elements, the outlying principles covering interconnection, cost, responsibilities, accountabilities, robustness, obligations, assessments and enabling the business allows each information asset within a system to be identified, understood and risk managed accordingly, to ensure that the system is protected; that is, information assured. By adhering to the model, security features, practices, procedures and architecture of information systems will accurately mediate, increase confidence, and help enforce security policies.
So essentially, IA is about measures to ensure the protection and defence of the organisations information assets (a combination of hardware, software and records) and does this by ensuring their availability, integrity, authentication, confidentiality and nonrepudiation. These measures include the provision for restoration of information assets, by incorporating protection, detection and reaction capabilities.
The principles, shown in Figure 1 in the orange areas shows facets required to ensure that IA can be managed effectively in for IS (Information Security) to operate effectively. IA is strategy focused, deals with management of information and its protection, covers a broad spectrum of information, and deals with the overall strategy of risk and mitigation at enterprise level. IA is about providing measures for information system restoration by incorporating protection, detection and reaction. Examples of such measures are Business Continuity, Disaster Recovery, Compliance, Privacy. There are subsets of IA. Information Security is a subset of IA and includes Information Protection and Cyber security.
Information Security
Information Security is more tools and tactics focused, and closer to the technology and henceforth operations, applications and infrastructure. There are three key concepts held in Information Security focusing on CIA Triad (Confidentiality, Integrity and Availability). Added to this are other definitions such as Interception, Modification, Interception and Fabrication, and the concepts of Possession, Authenticity and Utility (which was defined by Donn B. Parker and known as the Parkerian Hexad ). Examples of information security can be associated with Antivirus, Firewalls, IDSs, VPNs, Pen Testing and Vulnerability Analysis.
So, Information Security covers any information on any storage, and any medium from any technology. This is whether the information is on paper or stored in an encrypted document.
Information Protection
Information Protection, a subset of information security is related to the protection of confidentiality and integrity, and concerns policy, physical and technical controls, monitoring, classification of information. Information Protection also covers regulations, laws and rules, particularly related to the management of sensitive information, such as PII (personally identifiable information), and personal information.
Cybersecurity
Cybersecurity is a subset of Information security with Information protection. Table 1 shows the definitions from NIST .
| Definition | Description |
| Cybersecurity | “The ability to protect or defend the use of cyberspace from cyber attacks” |
| Cyberspace | “A global domain within the information environment consisting of the interdependent network of information systems infrastructures.Note. This includes internet, telecommunications networks, computer systems and embedded processors and controllers.” |
| Table 1: Cybersecurity and Cyberspace definitions. | |
Concepts
Information held is of critical importance to the organisation. Standards needs to be follows in order for a framework to be put into place for managing information. There are standards which will be described further in this paper. Standards allow better security controls to be put in place that is appropriate to your business.
Historically, information security, or INFOSEC, has been called a number of things. From Data Security, IT Security, and IA. Regardless of the definitions, the information that is stored on computers is worth more than the computers themselves. And, even those these terms have been used interchangeably, they are inextricably linked, and the characteristics of information that must be protected remain the same. They are Confidentiality, Integrity and Availability. These three are commonly called the CIA triad, and CIA is probably the most recognised acronym in the security industry. This triad applies whether the data is in storage, processing or transit and is described further in this section. There are alternative models, such as Parkerian hexad (which concerns Confidentiality, Possession or Control, Integrity, Authenticity, Availability and Utility, and non-Repudiation).
Confidentiality
Application of the Confidentiality principle ensures only authorised users with sufficient privileges can manage that information (use, copy, access). Authentication works in conjunction with confidentiality, in that if the user is not authenticated by a system to access relevant information, they will be refused access to that information. So, from a perspective of IA, information should be shared only among authorised persons or organisations. Because confidentiality disclosures can take place by printing, word of mouth, emailing, copying, or even creating documents, safeguards such as setting classification codes against that information, to determine the level of confidentiality needs to be in place for that information. Therefore, confidential data needs to be protected, by providing mechanisms to classify that data and audit access – however, confidentiality works closely with availability to that data from authorised staff workers.
Availability
Availability involves the amalgamation of processes involving systems that hold information, including the security protecting it, and making the information readily available to authorised users. This means that although a secure computer must restrict access attempts from unauthorised users, that same secure computer must allow immediate and timely access to authorised users. For example, authorised staff must be able to access records on a secure computer in a timely manner, as well as being able to access services available from the core business functions.
Authentication
There are a number of examples relevant to Authentication:
- When a person accesses a device at which will connect to the company infrastructure
- When a networked computer accesses a server located within the company infrastructure
- When a person / device / system interacts with a device which has access to company resources
- When a person / device / system interacts with a WIFI connection located in any part of the company.
There are many more examples. Note however, that authentication does not determine what the individual can and cannot do; authentication identifies and verifies who the person, or the system is.
Integrity
Integrity ensures that the stored information is correct, and that no unauthorised persons, or software has altered the information. Integrity of information is to say that the information is complete, authentic and is accurate for its purpose. Integrity not only applies to whether the information is correct, but whether that same information is reliable and can be trusted. Information can be at risk of modification, or alteration, or both – this affects its integrity. If, for example a copy of a sensitive document is made, then emailed, doing this threatens both the integrity and confidentiality of the document. By defining Integrity as part of IA protects information, and therefore prevents that information from being corrupted, altered, deleted or recreated without proper authorisation. For any organisation, there are many examples in which their key asset, information, could have its integrity affected:
- When staff make mistakes in creating information (for example, non-classification of confidential information)
- When information is stolen (cyber-crime), or accessed by unauthorised access by staff, which also affects confidentiality
- When there is a software failure resulting in corrupted information, which also affects availability
In terms of the CIA triad, Integrity is probably more critical than confidentiality, or availability. Measures to protect integrity includes error checking methods, such as checksums, file-hashing; and in terms of data processing could even include validation checking.
Non-Repudiation
Non-Repudiation means to validate the integrity of a digital signature’s transmission; starting from where it originated and ending where it arrives; and provides the guarantee that no-one can deny the authenticity of a signature on a document, or deny that a message did not come from where it was sent. For example, a digital signature is used to ensure that a message, or document, has been electronically signed by a specific individual, and to ensure that subsequently that same person cannot deny they electronically signed the document. Non-Repudiation also works for e-mail; for example, tracking solutions that will ensure that the sender cannot deny sending a message, or that the recipient cannot deny they received the message. For example, non-repudiation is required particularly in posting contractual information which needs to be signed for or when information that requires confirmation of delivery is required. Failure in doing this means lack of trace-ability leading to difficult audit situations in the event of an unauthorised breach of information.
So where does Office365 help?
There are a number of features in the Office 365 suite that may help concerning management of email security and data security. For email security, you can create filtering policies using the Exchange Online Protection features, which is within the Security Compliance Options section (advanced threats, also known as Advanced Threat Protection – ATP). This provides features to ensure safe attachments, and safe links. These provide methods for Malware removal, to prevent Phishing attacks and will even remove links from emails which are known as bad sites, without unduly tampering with the remainder of the email. For data security, there are Data Governance options concerning data import, retention policies, and integrity features such as DLP (Data Loss Prevention are policies designed to help protect and manage the company information across various locations). This allows the automation of security to enable blocking access to data, or to encrypt documents, or even inform users if content is saved to the wrong location.
Summary
IA is about protection of data; the identification, understanding and managing risk. The elements of IA include Governance, Business Continuity, Information Security, Privacy, Disaster Recovery and Risk Management. That means ensuring that data is not modified, or transferred. That means that data is not destroyed. That means that ensuring the data is available to the intended, and that the methods by which that data is accessed is defined (through authentication). IA includes all information irrespective of the media used to create, store and destroy. This article, whilst written generically, is designed to make you think of Information Assurance and how important it is to define standards to ensure the protection of company information.
About the Author:
GEOFF EVELYN, is an Office Services and Systems MVP. Follow him on twitter HERE.
References
COREY SCHOU, S. H. The MSR Model of Information Assurance. Information Assurance Handbook : Effective Computer Security and Risk Management Strategies. McGraw Hill Education.
WATKINS, S. G. 2010. INFORMATION ASSETS. In: CALDER, A. & WATKINS, S. G. (eds.) Information Security Risk Management for ISO27001/ISO27002. IT Governance Publishing.
ANDRESS, J. 2014. The basics of information security: understanding the fundamentals of InfoSec in theory and practice, Syngress.
KISSEL, R. NISTIR 7298, Revision 2, Glossary of Key Information Terms. Available: http://nvlpubs.nist.gov/nistpubs/ir/2013/NIST.IR.7298r2.pdf.