INTRO
As infrastructures get ever more complex, managing security becomes a significant issue. Alerts and logs are coming from many different systems, in as many different formats, and it’s important that the right information is delivered to the right person in order to make the right decision to prevent a security breach.
That ‘right time’ information model is critical, and it needs tooling that can bring all these information sources and events into one place. Security Information and Event Management, SIEM, is a rapidly growing part of the enterprise security market, building and delivering smart security dashboards that analyze and priorities these messages, using a mix of log file analysis and machine learning. In a complex threat environment, modern data centers need a SIEM to operate effectively, sat next to your application and network monitoring tools and helping manage your response to incidents and warnings
AZURE SENTINEL
Microsoft recently launched Azure Sentinel, its approach to modern SIEM. Working across on-premises and in-cloud infrastructure, it’s intended to be easy to set up, low maintenance, and easy to use. By building on cloud-scale data collection, and on Microsoft’s own threat detection tools, Azure Sentinel can automate response using orchestration across your entire estate. It’s software-as-a-service so it’s scalable, and you only pay for the resources you use. The biggest advantage is its support for Microsoft security graph
Building on the full range of existing Azure services, Azure Sentinel natively incorporates proven foundations, like Log Analytics, and Logic Apps. Azure Sentinel enriches your investigation and detection with AI, and provides Microsoft’s threat intelligence stream and enables you to bring your own threat intelligence.
GETTING STARTED
1 – Go into the Azure portal
2 – Click on Create a resources
3 – Search of Azure sentinel
4 – Click on Create
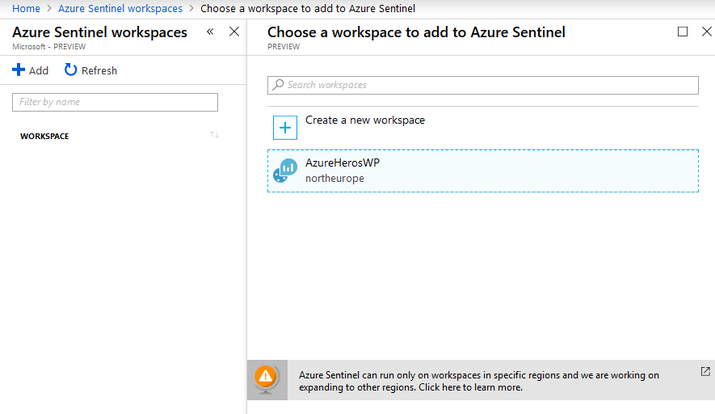
5 – Azure Sentinel WorkSpaces window will be open
6 – Click on Create Workspace
7 – Click on Add button
8 – Enter the required information in our example i choose “AzureHerosWP”
Azure Sentinel can run on workspaces that are deployed in any of the following regions:
- Australia Southeast
- Canada Central
- Central India
- East US
- East US 2 EUAP (Canary)
- Japan East
- Southeast Asia
- UK South
- West Europe
- West US 2
10 – In my case I will connect it with Azure Virtual Machines which I already have
11 – Click on desired virtual machine then click on Connect
12 – Connect the Workspace to Azure Sentinel
13 – From the dashboard itself you can get analysis of what’s happening on your environment, fusion technique used here to correlate alerts into cases you reduce noise and minimize the number of alerts you have to review and investigate
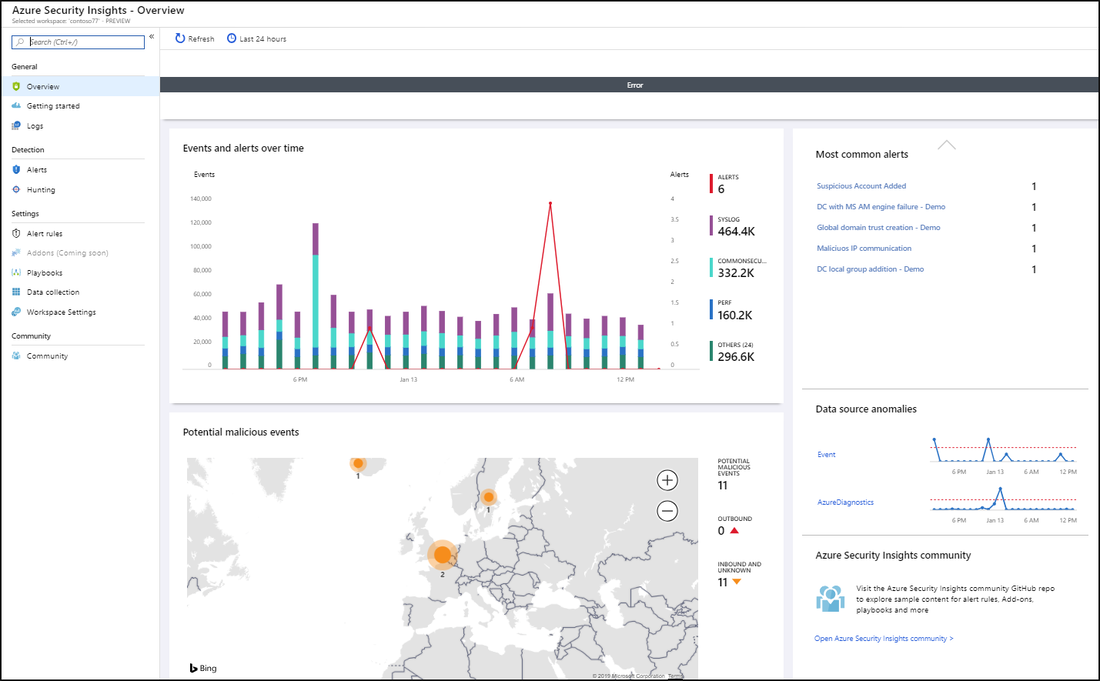
Use Toolbar to
- Get how many events you got over the time period selected
- Get The alerts that were triggered
- Get The Event status : How many are open,in progress, and closed

Finally, to start hunting:
Create detection rules then start Respond to threats by creating playbook to run automatically when an alert is triggered when you configure the playbook or Manually run a playbook from inside the alert, by clicking View playbooks and then selecting a playbook to run.
Ref:
https://docs.microsoft.com/en-us/azure/sentinel/
https://www.techrepublic.com/article/azure-sentinel-microsofts-thoroughly-modern-siem/