Azure AD LAPS (Local Administrator Password Solution) provides management of a single local administrator account on Azure Active Directory or local Active Directory joined devices. The password is then protected in AD while access to the password can be delegated to specific users.
The configuration and deployment of modern Azure AD LAPS is simplified with Microsoft Intune, once enabled in your tenant, a single configuration profile can be used to configure Windows LAPS (built into the latest version of Windows operating systems). The password can then be accessed and rotated manually through the Azure AD or Intune management portal.
In this tutorial, I am going to show you how to configure Azure AD LAPS from the Microsoft Intune management portal.
About LAPS with Intune
The Azure AD LAPS scenario is backed by the new Windows LAPS capabilities built directly into the Windows operating system. This means it can be quickly and easily deployed without the need for additional client software to be installed.
The downside to this comes in the form of the requirements. Windows LAPS is only supported in the latest operating systems, meaning if you are not current and consistent with Windows feature updates (which are a pain to some) you may be left with some devices not secured. Therefore, it is important the requirements are carefully considered to reap the security benefits that Azure AD LAPS with Intune can bring. Fundamentally it is all or nothing, if you leave a hole the hacker will find it.
The deployment of Azure AD LAPS is simplified using Microsoft Intune, however, for those with limited management capabilities, it can also be deployed via group policies, manually through registry keys or using Windows CSP settings in Intune. For whatever reason multiple deployment methods apply to a single machine, and the Windows CSP/Intune settings will always take precedence. Intune will always be the recommended choice, it is simple, the reporting features are good and it does not require line of sight to a domain controller.
Enable Azure AD LAPS
To support the implementation of Azure AD LAPS you must first enable Windows LAPS for Azure AD in the Azure AD management portal. To do this simply follow the below steps:
1. Login to https://aad.portal.azure.com/
2. Select Azure Active Directory, then Devices.
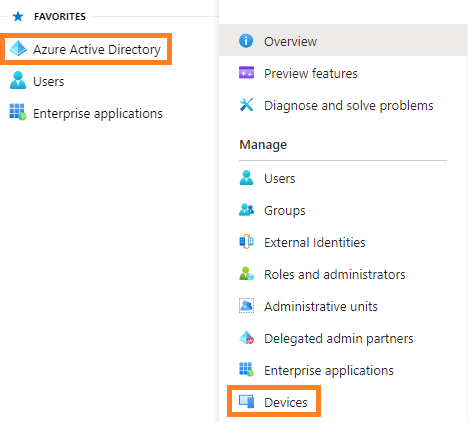
3. Select Device Settings.
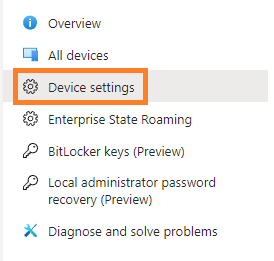
4. Set Enable Azure AD Local Administrator Password Solution (LAPS) to Yes, then click Save and the top.
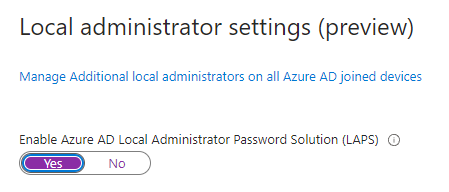
When this is complete, you will be ready to enable Azure AD LAPS on your devices. Also, behind the scenes, this will set the IsEnabled field for the localadminpassword setting to True in Microsoft Graph.
You should also know that when you enable Azure AD LAPS here, it will become available to store LAPS passwords for all devices. If you want to enable the setting to all devices, or just specific devices, that will be done with configuration profiles in the next step.
Create a LAPS configuration profile
Now LAPS is enabled for your tenant, you are now ready to create a configuration profile which will contain all the settings for Azure AD LAPS to apply to your devices.
1.Login to Intune https://intune.microsoft.com/.
2. Select Endpoint Security.
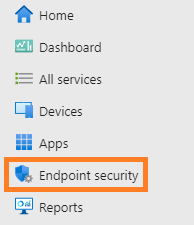
3. Then select Account Protection.
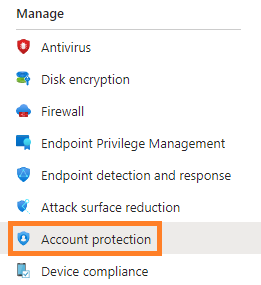
4. Click Create Policy to create a new Endpoint Protection Policy for Azure AD LAPS.
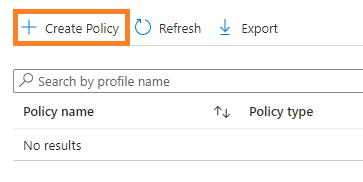
5. In the pop-out window, select Windows LAPS from the drop-down list and click Create.
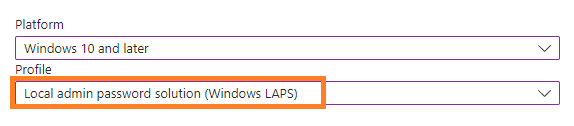
6. Choose a meaningful policy name and click Next.
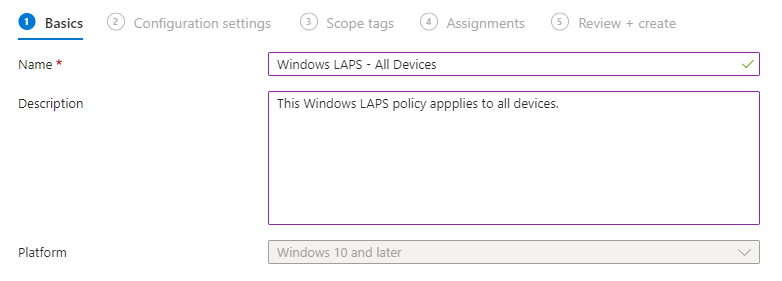
7. Define your Azure AD LAPS configuration settings. Use my settings as recommended:
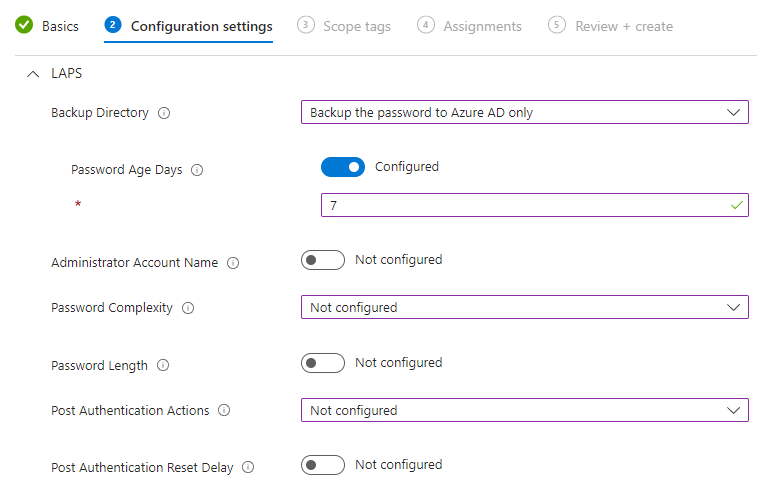
Some settings above have been left as default, the values will default as below:
- Administrator Account Name: The default admin SID (which is consistent across all devices) will be used, regardless if the account has been renamed.
- Password Complexity: Large letters + small letters + numbers + special characters
- Password Length: 14 characters
- Post Authentication Actions: Reset the password and logoff the managed account
- Post Authentication Reset Delay: 24 hours.
When you are done, click Next.
8. Define any scope tags in the Scope tags section and click Next.
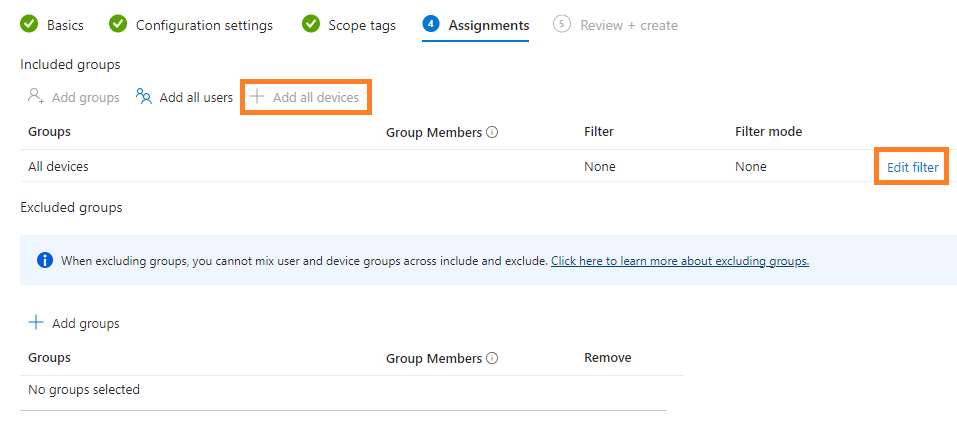
10. Finally review your settings and click Create.
Check if Azure AD LAPS is successful
When deploying Azure AD LAPS there is no need to reboot your devices, unlike the previous version of LAPS where a reboot would be required to deploy the MSI via GPO. This means the next time the policy applies to your device, then LAPS will be configured.
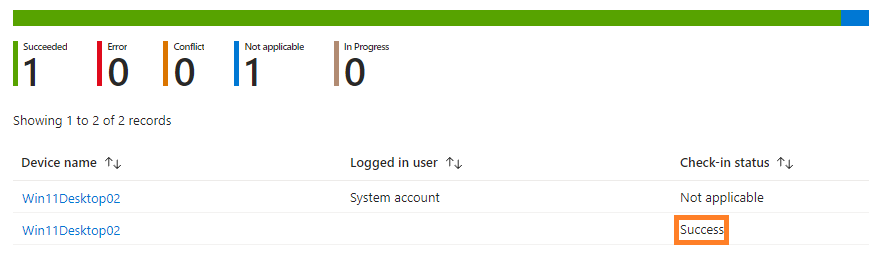
You can verify whether the policy has deployed as expected from the policy report window:
From the Intune portal: Endpoint security > Account protection > *Your LAPS policy* > View Report.
Windows Event Logs
You will see Event ID 10022 for LAPS once it has been deployed successfully on the client, located at:
Application and Services Logs > Microsoft > Windows > LAPS
The log will contain information on the configuration of LAPS, this can help you determine the correct policy is applied if you have different configurations for different groups of devices.,
The current LAPS policy is configured as follows:
Policy source: CSP
Backup directory: Azure Active Directory
Local administrator account name:
Password age in days: 7
Password complexity: 4
Password length: 14
Post authentication grace period (hours): 24
Post authentication actions: 0x3
See https://go.microsoft.com/fwlink/?linkid=2220550 for more information.
View and rotate Azure AD LAPS password
Viewing and rotating the LAPS password for a device can be done quickly and easily through the Azure AD portal or the Intune portal.
Azure AD Portal
To view the LAPS password from the Azure AD Portal, follow these steps:
Devices > Local administrator password recovery > Select your Device > Show local Administrator password.
Intune Portal
To view the LAPS password from the Intune Portal, follow these steps:
Devices > All devices > Select your device > Local Admin password > Show local admin password.
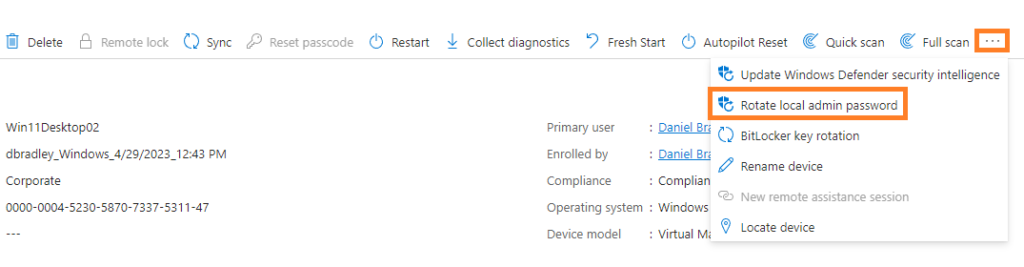
To rotate the password before the set expiration period, select the device from within Intune, click on the 3 dots at the top right then click Rotate local admin password.
LAPS will also block external attempts to change the password, including when you use the ‘reset password’ function in Azure for virtual machines. The following log will appear in the Windows event log:
Event ID: 10031
LAPS blocked an external request that tried to modify the password of the current managed account.
Account name: %accountname%
Account RID: 0x1F4
See https://go.microsoft.com/fwlink/?linkid=2220550 for more information.
Enjoy more great Azure Week blogs here.
About the Author:
My name is Daniel Bradley and I work with Microsoft 365 and Azure as an Engineer and Consultant. I enjoy writing technical content for you and engaging with the community.
Reference:
Bradley, D. (2023). How to Deploy Azure AD LAPS with Intune Step by Step. Available at: https://ourcloudnetwork.com/how-to-deploy-azure-ad-laps-with-intune-step-by-step/ [Accessed: 13th July 2023].











