Deployment Guide
In this blog post, I will be talking about the differences between Azure ATP vs ATA. You can also read about Azure advanced threat protection deployment, Azure ATP and Windows Defender ATP integration, and Azure advanced threat protection lateral movement.
AZURE ADVANCED THREAT PROTECTION AZURE ATP
If you’ve ever used Microsoft advanced threat analytics (a.k.a ATA) before, you would be surprised or confused to hear about Azure advanced threat protection or Azure ATP. They both serve almost the same purpose, which is analyzing traffic coming from your on-premises domain controllers and detect anomalies.
So, why Microsoft decided to offer the same functionality under a different name and as a cloud offering? There are two parts here, the new name/brand, and the cloud offering part.
DIFFERENT BRANDING, SAME FUNCTIONALITY?
Let us start with the name, from ATA to ATP. If you notice, Microsoft is launching their new integrating security model in Office 365 and Windows under the ATP umbrella. In Office 365, we have the Microsoft Office 365 advanced threat protection or Office 365 ATP, that helps detecting zero-day attacks and suspicious links via Office 365 safe attachment and safe links features. This helps detecting malware coming from email and SharePoint.
Microsoft also launched their Endpoint Detect and Response (EDR) solution on Windows under the name of Windows defender advanced threat protection or Windows Defender ATP to help detect persistent malware at the endpoint level.
What is missing is a cloud solution to detect anomalies and lateral movement for identities, which Microsoft offered previously under the name of Advanced Threat Analytics or ATA. It is an on-premises solution that can collect data from on-premises domain controllers and is not integrated with any of the other ATP products in Office 365 and Windows.
I believe Microsoft wants to complete the missing piece in the cloud ATP family, by offering identity behavioral piece as a cloud service, and give it another ATP name. Hence the name Azure advanced threat protection or Azure ATP.
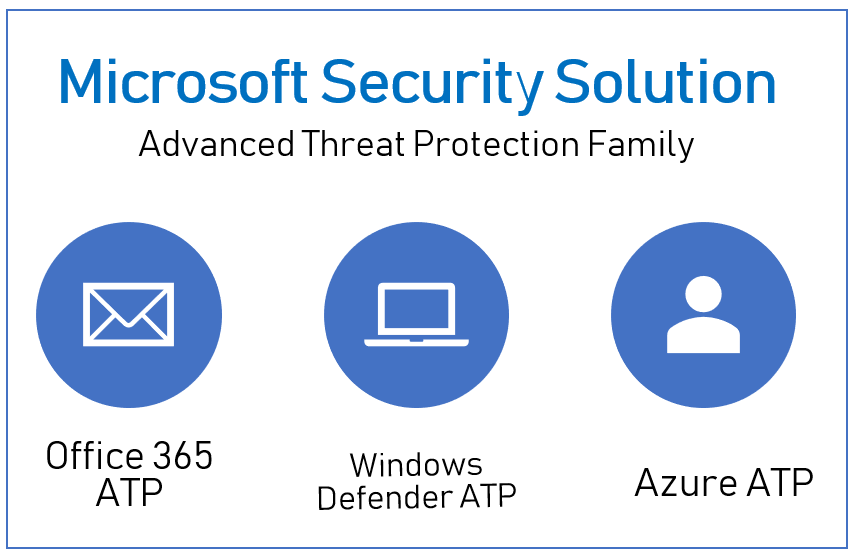
Microsoft Security Solution
CLOUD OFFERING? ATA AS A SERVICE?
The power of any security solution is its ability to integrate with other sources and security solutions. No one solution can give you the whole picture, as an anomaly in an authentication transaction might seems low risk, but if you add to this that the machine from which the authentication happened is infected by zero-day malware, then we can be sure that this is a high-risk transaction. Integration is a key thing, and Microsoft knows that. Currently ATA cannot integrate with other Microsoft security solutions.
Hybrid cloud and hybrid IT is now considered the end goal for many enterprises. 9 out of 10 IT managers report there will always be data in the cloud, and data on-premises for different security or privacy reasons. To better serve such hybrid IT, a good security solution should track any compromised identity whether this happen first on-premises and propagate to cloud, or vise-versa. Currently ATA can only read from on-premises domain controllers and can integrate with SIEM, but what about collecting data from Azure AD for example, the missing piece in this hybrid story.
Furthermore, no one can deny that deploying ATA on-premises means that you have to worry about the ATA center and that mongo DB inside. Offloading the whole ATA center functionality to the cloud is a welcome thing always. You can think of Azure ATP as (ATA center as a service), with a lot more improvements. With the cloud, we will get better availability, performance improvement, availability and functionality that are hard to achieve on-premises.
Think about it, to complete the ATP family that Microsoft offer in the cloud with Office 365 ATP and Windows Defender ATP, Microsoft ATA should be moved to the cloud with a new brand (Azure ATP), so that Microsoft can innovate more quickly with it, and enable integration between the three ATP services.
ATP VS ATA
AZURE ATP VS ATA ARCHITECTURE
I deployed Microsoft ATA in a big environment when ATA service was first announced, and I really liked the product. I was wondering if there would be a cloud offering for this, where traffic from my domain controllers can be analyzed in the cloud, instead of maintaining the mongo DB in the ATA center on-premises. This is exactly what happened recently when Microsoft announced such offering under the name of Azure ATP.
In ATA world, you would have either ATA gateways (port mirroring for your domain controller) or ATA lightweight gateway agent deployed directly on your domain controllers. In both ways, traffic will be coming to your domain controllers will be captured and sent to a centralized on-premises server called ATA Center, that aggregate that traffic into an internal mongo database.
What Microsoft is doing now is offering that ATA center as a service in the cloud. So, traffic from your domain controllers (either from a gateway or agent on DC), will be sent directly to a cloud service to be analyzed, and no need to maintain the on-premise mongo database anymore, eliminated by that the role of ATA center.
For me, this is a better approach, as it allows for more integration with other Azure security products, and it reduces the maintenance work you should do to the on-premise ATA Center.
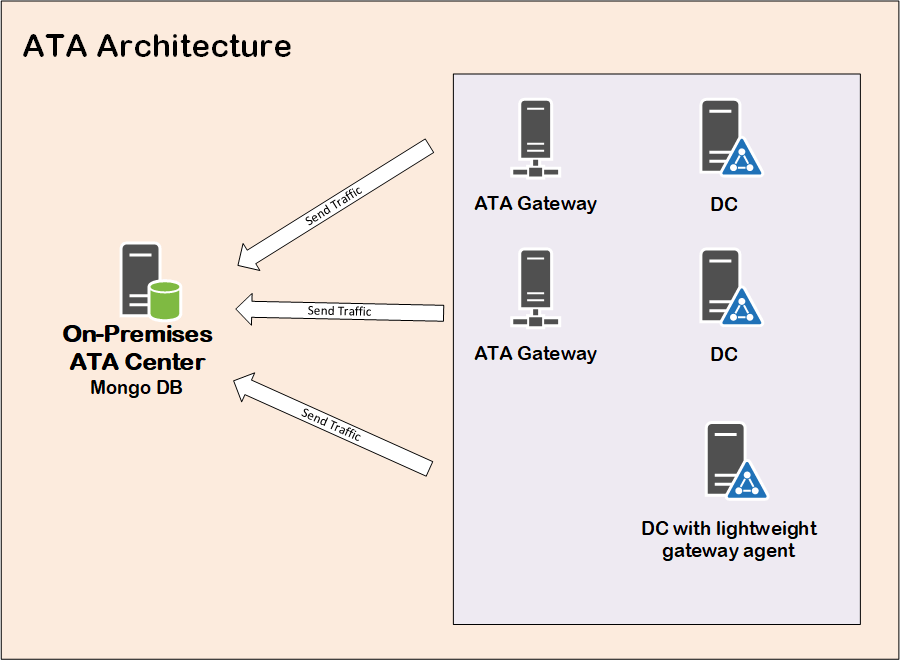
ATA Architecture
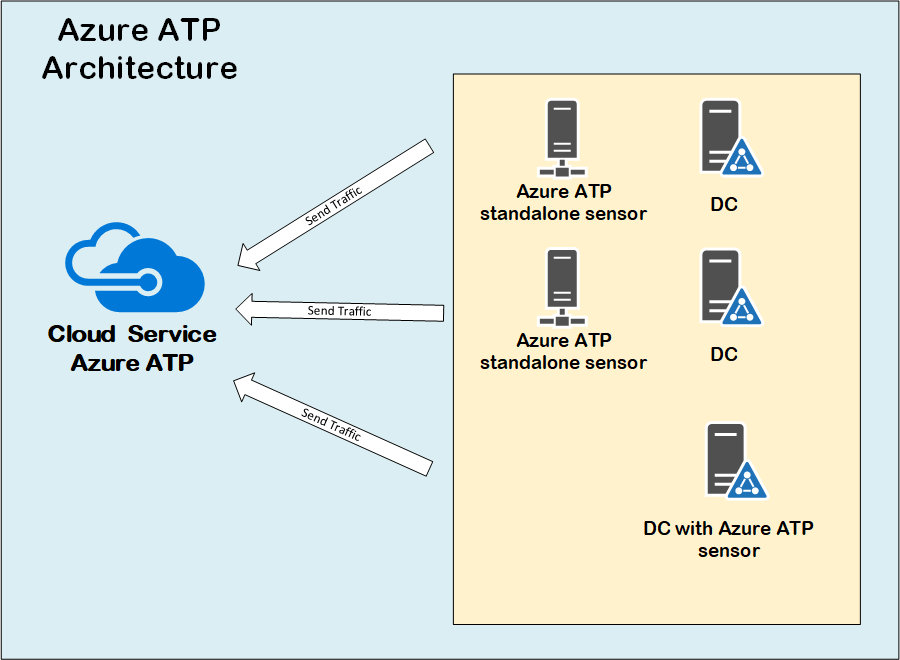
Azure ATP Architecture
AZURE ATP VS ATA PERFORMANCE
While Azure ATP is considered an evolution of the previous Microsoft Advanced Threat Analytics (a.k.a Microsoft ATA), it is not like Microsoft just moved the service to the cloud to help you reduce the infrastructure footprint on-premises. Instead, Azure ATP is re-engineered completely to offer better, salable and more integrated solution with other Microsoft cloud solutions as we will see later.
Take the agent for example, the Azure ATP sensor is 10 times more efficient in terms of performance than the ATA lightweight gateway as reported by Microsoft. If you have a box with the two agents, you can see what I mean. Thanks to the new parsing platform that comes with Azure ATP sensors, you can rest assure that your domain controllers will not be under pressure when deploying Azure ATP sensors with the proper capacity planning.
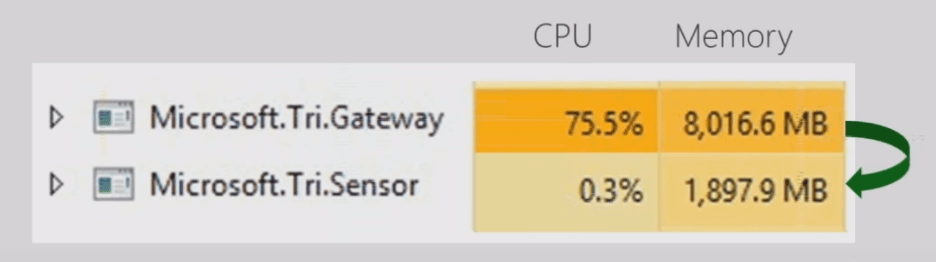
CPU and Memory
Microsoft admits that it was not easy to think of another name for the “Gateway” as part of the new Azure ATP branding. They want to make it clear to everyone that they re-engineered the agents completely with better parsing platform and up to 10 times performance improvement. Finally, they come up with the name (Sensor) instead of (Gateway).
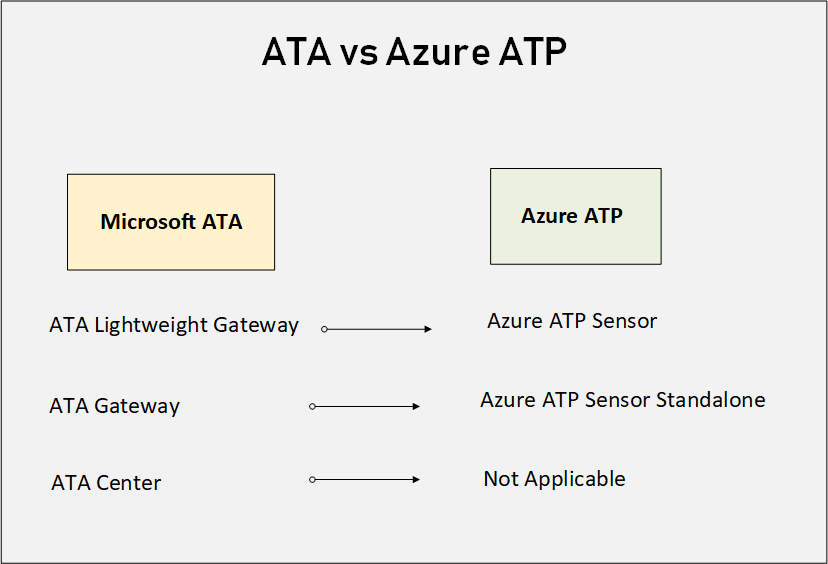
ATA vs Azure ATP
AZURE ATP VS ATA: INTEGRATION
Azure ATP is fully integrated with Windows Defender ATP, so if you have a tenant with Microsoft Windows Defender ATP licenses, you will see in the Azure ATP management portal an option to integrate with Windows Defender ATP.
Microsoft also is investing in doing more and more integrations to get more logs from cloud sources, so that a compromised identity on-premise moving to the cloud can be inspected by Azure AP, and vise-versa.
TIME TO SHIFT FROM ATA TO AZURE ATP
I was not sure whether I should move from ATA to Azure ATP as I already invested in deploying a lot of ATA gateway servers already. I heard about the performance improvement that comes with Azure ATP sensors, but still I was not sure.
The good news is that you can deploy Azure ATP sensors alongside with ATA agents. In my case, the same server acts as Azure ATP sensor standalone server sending traffic to the cloud, and as ATA gateway sending traffic to my on-premises ATA center. This gives me the chance to deploy Azure ATP sensors without deploying new servers but using the existing servers I use for ATA.
Since I am using Windows Defender ATP also in my tenant, and as soon as I turn on the integration between Azure ATP and Windows defender ATP, I realized that the future is Azure ATP. First, I was afraid that this integration is hard to do, but it is a matter of turning a switch in the management portal, and I got the full integration between the two ATP services.
I cannot emphasis how amazing this integration is. You can pivot from an identity inside Azure ATP to the same identity in the context of Windows defender ATP. What this give you is the full picture about the attack happening inside your environment and significantly reduce false positives.
I heard from Microsoft that all new features are coming to Azure ATP more quickly as it is a pure cloud offering, and Microsoft is also planning to add more integration between Azure ATP and other cloud services. I did the migration, and I am really impressed, so what are you waiting for?!
Reference: Hasayen, A. (2018). Azure Advanced Threat Protection Azure ATP Vs ATA. Available at: https://blog.ahasayen.com/azure-advanced-threat-protection-lateral-movement/ [Accessed: 10 May 2018]